1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
ciphertext = bytes(x & 0xFF for x in [0x7F, 41, 0x20, -23, 53, 0xFFFFFF8F, -59, 0x9A, 5, 16, 52, 0xBC, 91, 150, 43, 0xA3, 140, 170, 0x9E, 36, 0x91, 140, 0xD3, 17, 18, 0x4F, 200, 0xB1, 0x7A, 78, 0xDB, 0xF7])
key = bytes(x & 0xFF for x in [-95,109,22,-2,26,-6,48,95,-41,126,94,-98,-20,107,-97,-35])
iv = bytes([0,2,4,6,8,10,12,14,16,18,20,22,24,26,28,30])
cipher = AES.new(key, AES.MODE_CBC, iv)
plaintext = unpad(cipher.decrypt(ciphertext), AES.block_size).decode("utf-8")
print(plaintext)
|
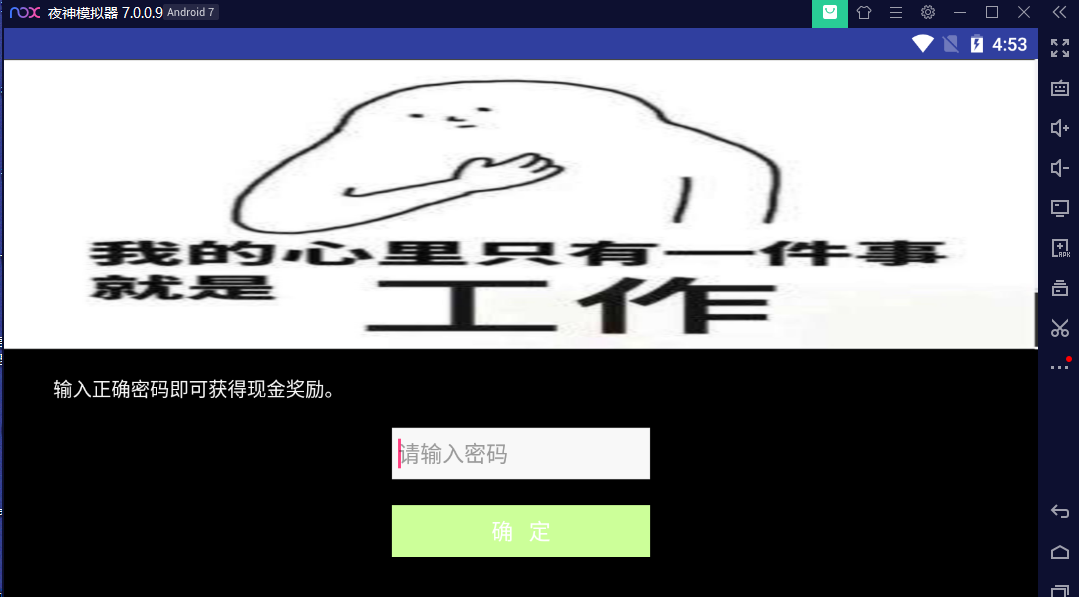 jeb 反编译找到MainActivity
jeb 反编译找到MainActivity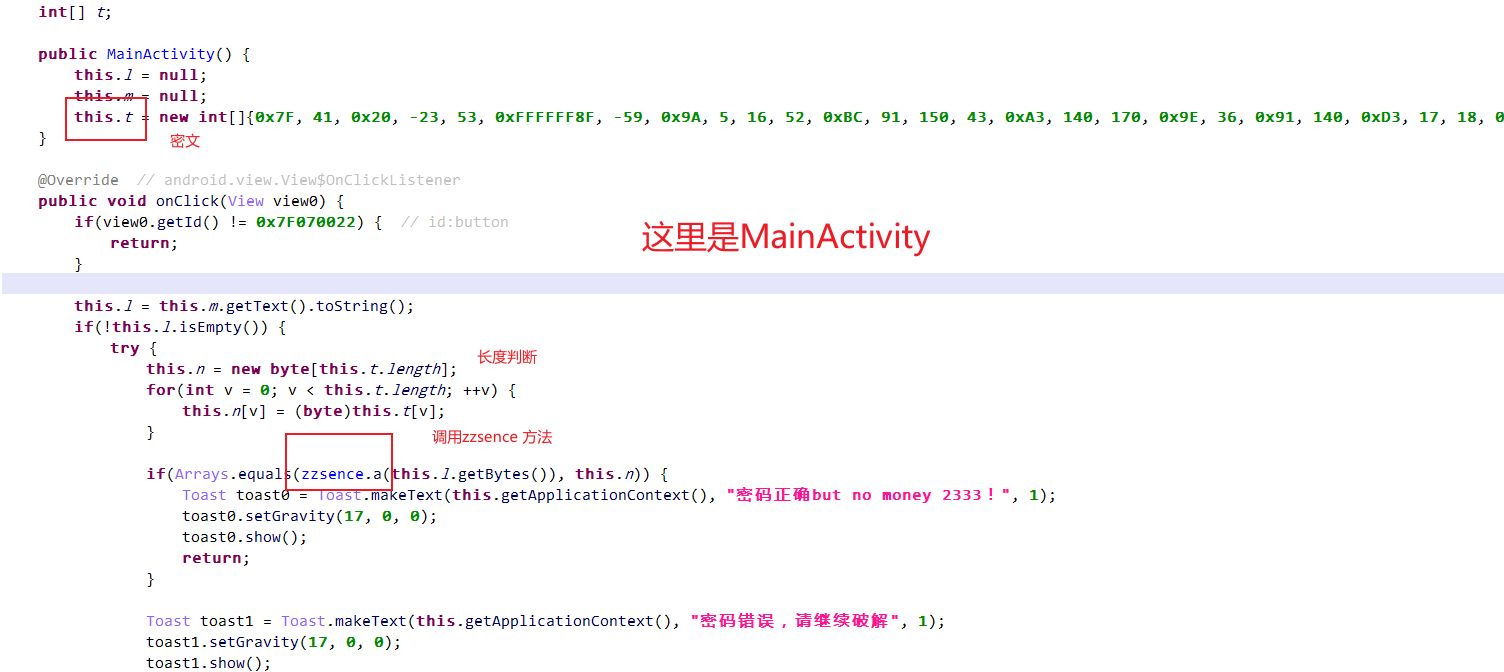 进入zzsence方法
进入zzsence方法 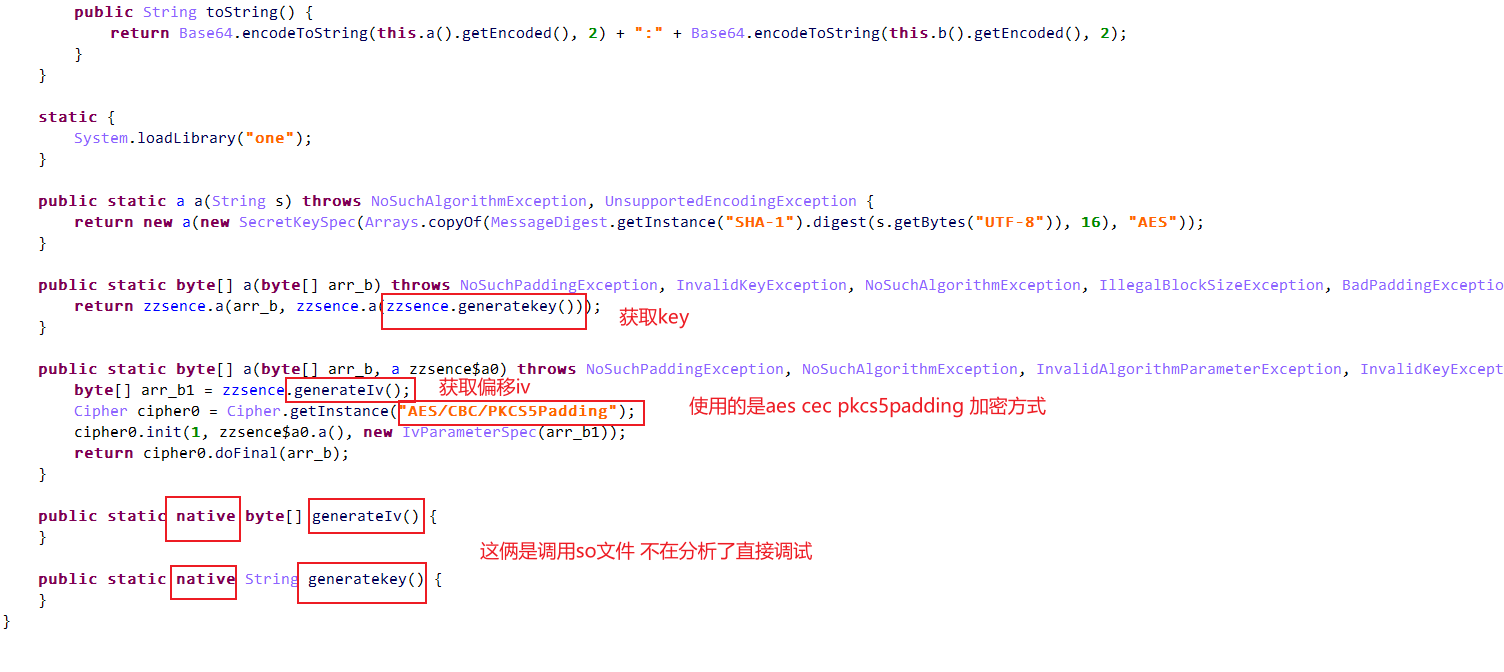
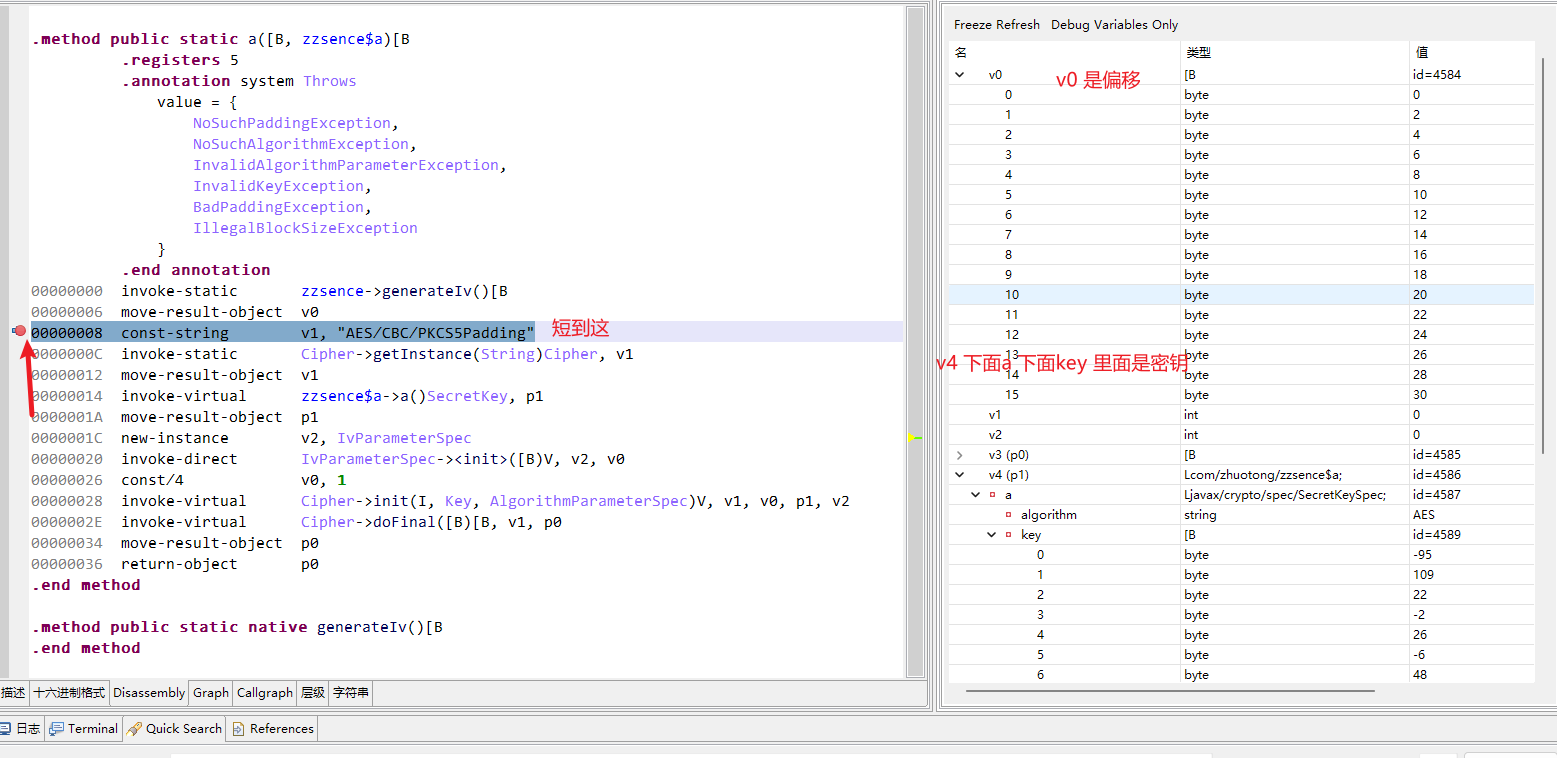 编写脚本
编写脚本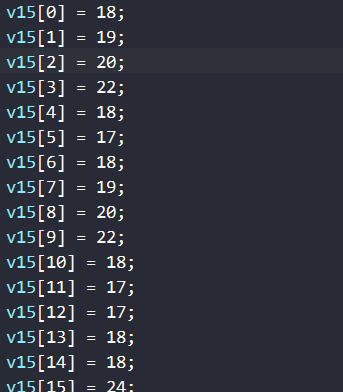 一段 key 和enc[abi:cxx11] 进行判断
一段 key 和enc[abi:cxx11] 进行判断
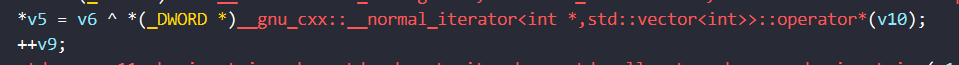 加密逻辑 z3 一把梭哈
加密逻辑 z3 一把梭哈