New Star Ctf Re
本文最后更新于:2023年10月19日 上午
New Star Ctf Re
New Star Ctf Week1 Re
easy_RE
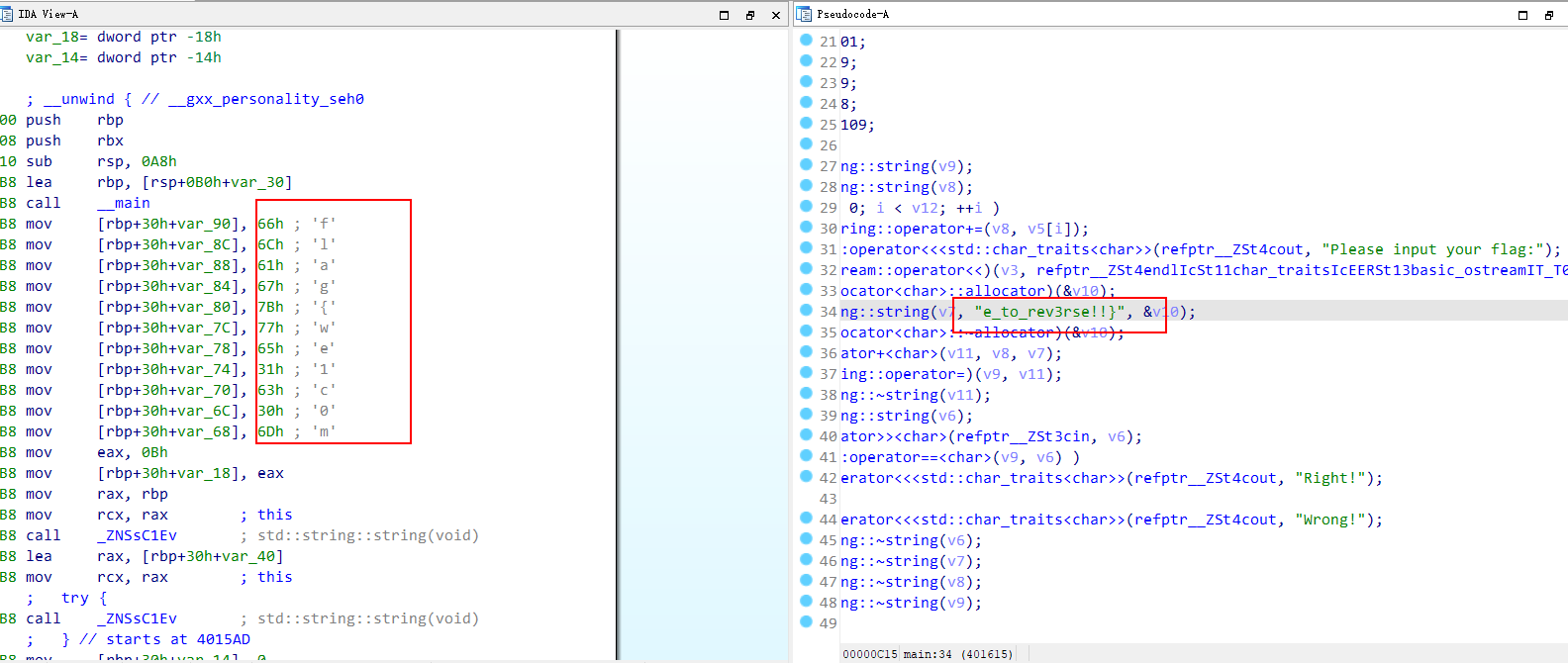
flag flag{welc0me_to_rev3rse!!}
咳
upx 壳
upx -d 文件
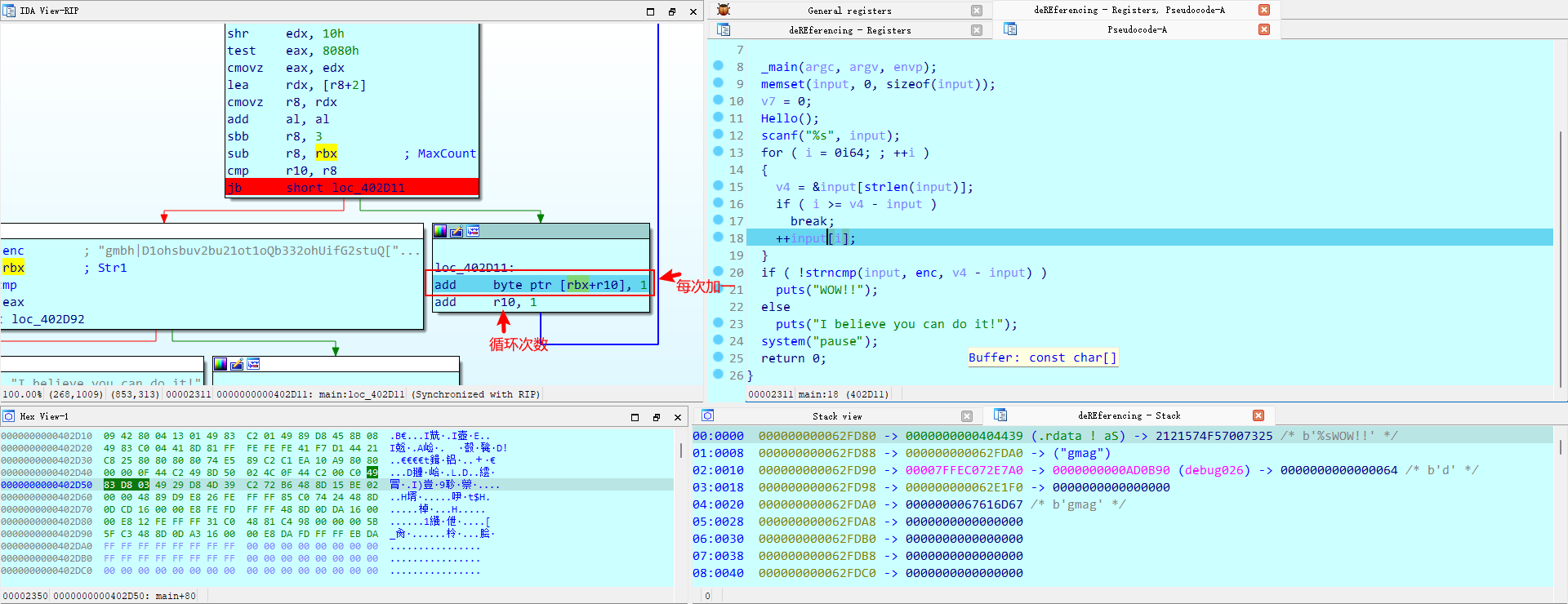
1 | |
flag flag{C0ngratu1at10ns0nPa221ngTheF1rstPZGALAXY1eve1}
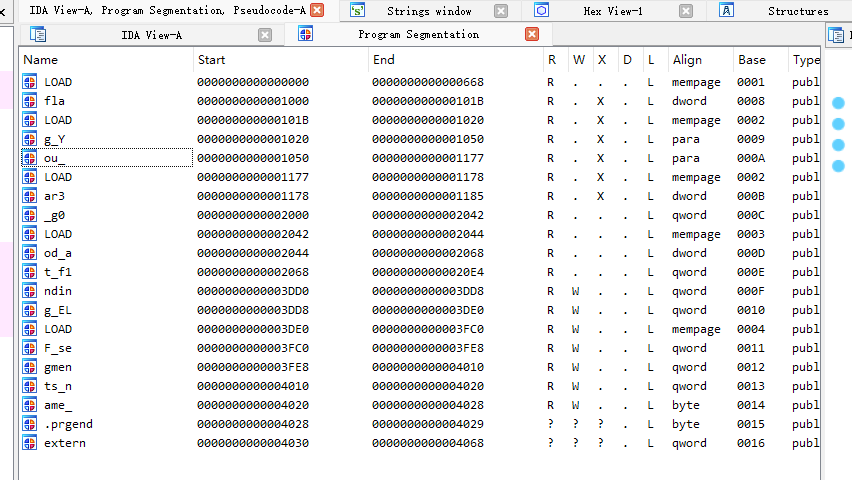
Segments
tips:IDA的Segments窗口要怎么打开呢(注:flag格式为flag{…})
shift+f7
flag flag{You_ar3_g0od_at_f1nding_ELF_segments_name}**
ELF
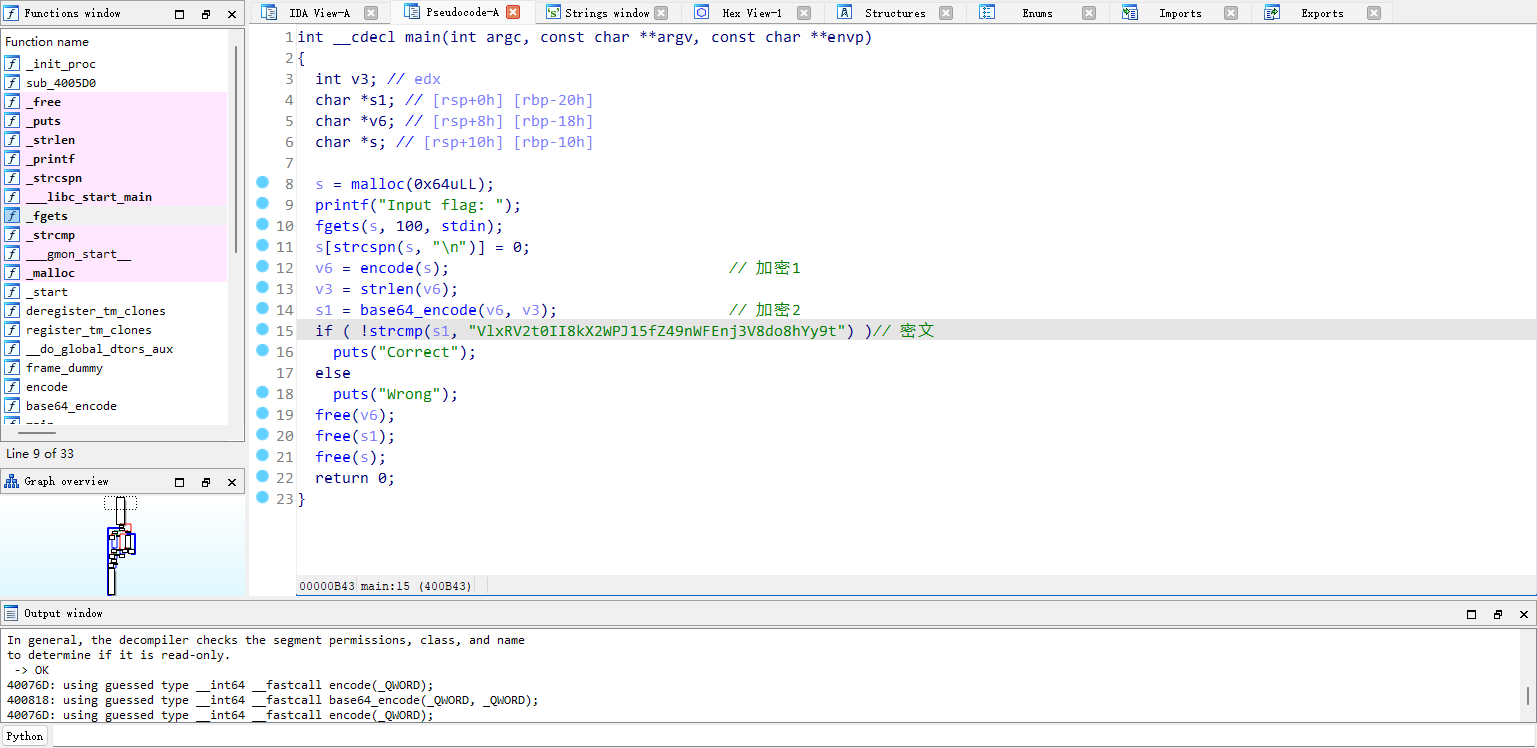
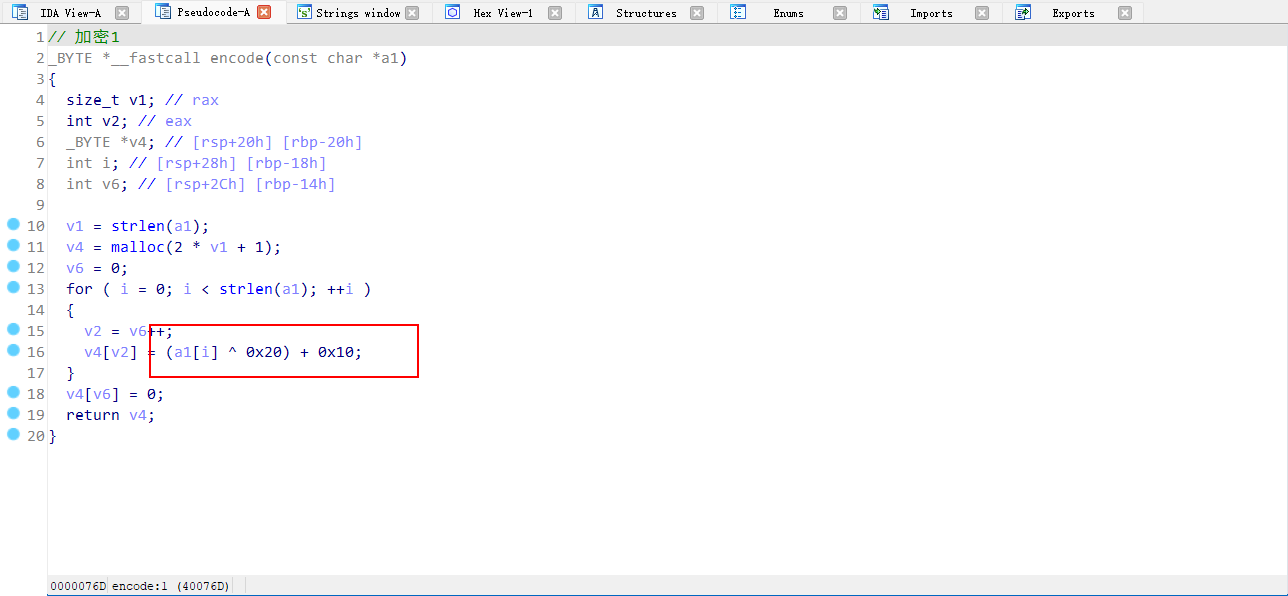
加密2是正常的base64
使用cyberCYBER
https://huajien.gitee.io/cyber
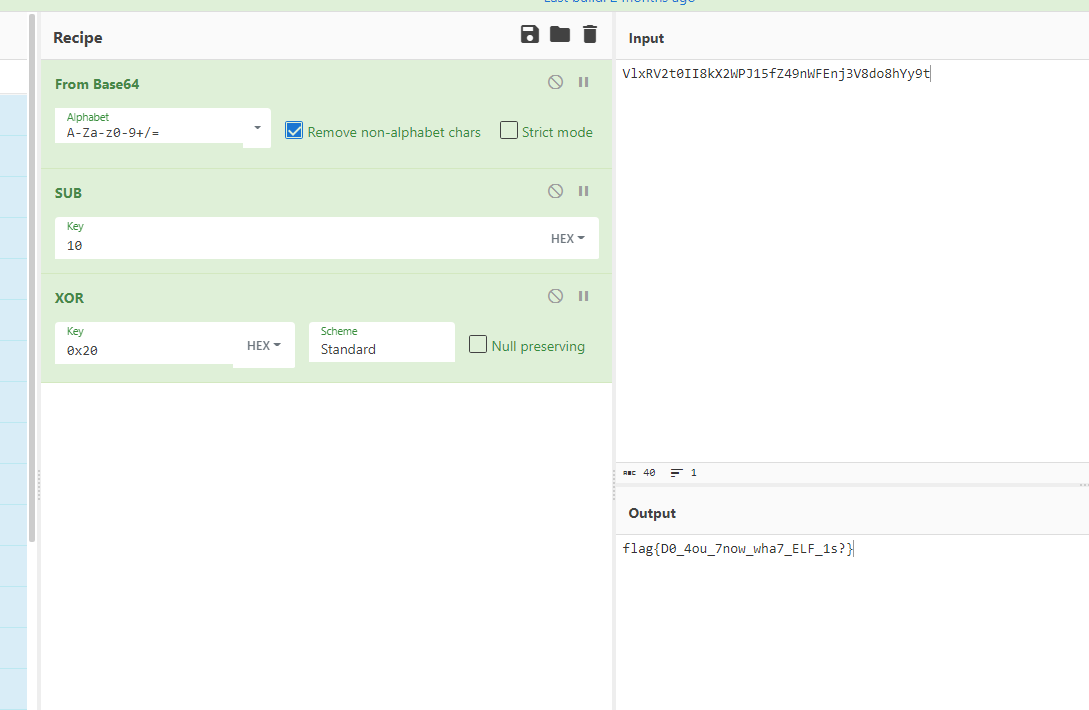
flag FLAG{D0_40U_7NOW_WHA7_ELF_1S?]
Endian
根据标题猜测是小端序
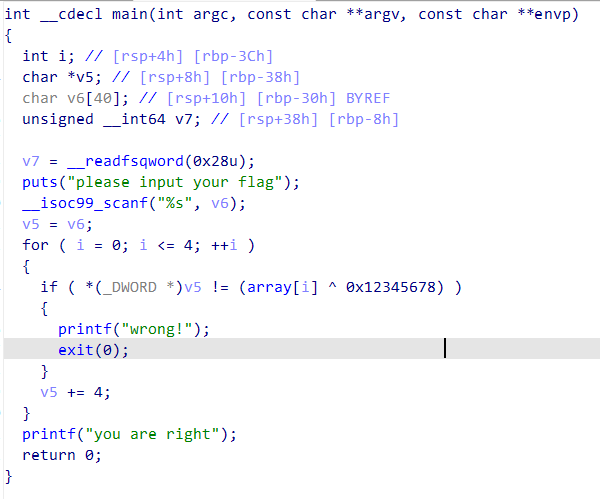
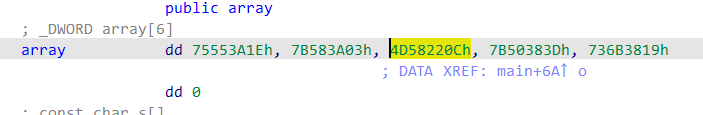
1 | |
flag flag{llittl_Endian_a}
AndroXor
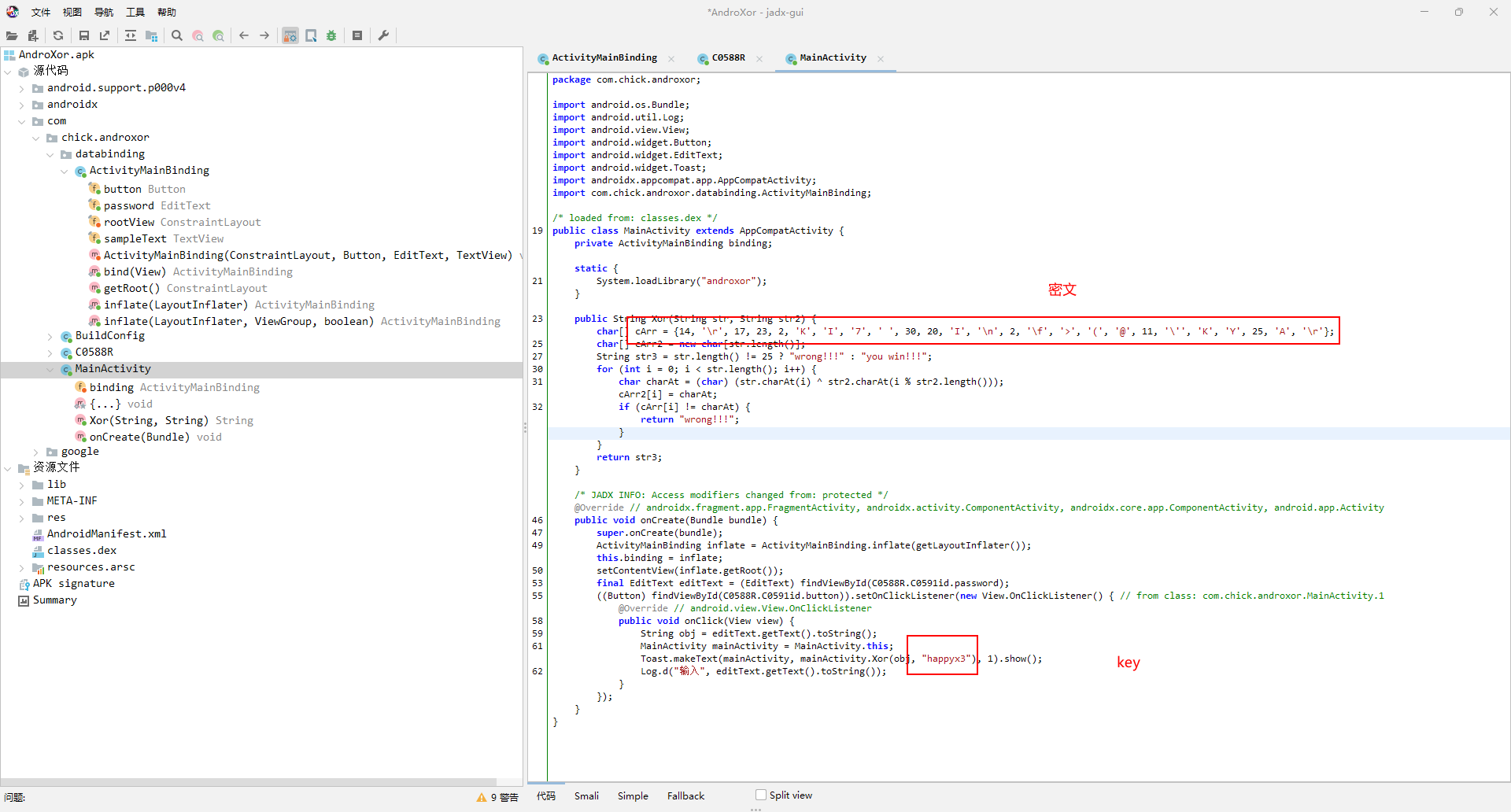
1 | |
flag flag{3z_And0r1d_X0r_x1x1}
EzPE
文件头他这是PZ 改为MZ
pe 结构到LONG AddressOfNewExeHeader
应该是0x80他这边是0x90改为0x80即可运行
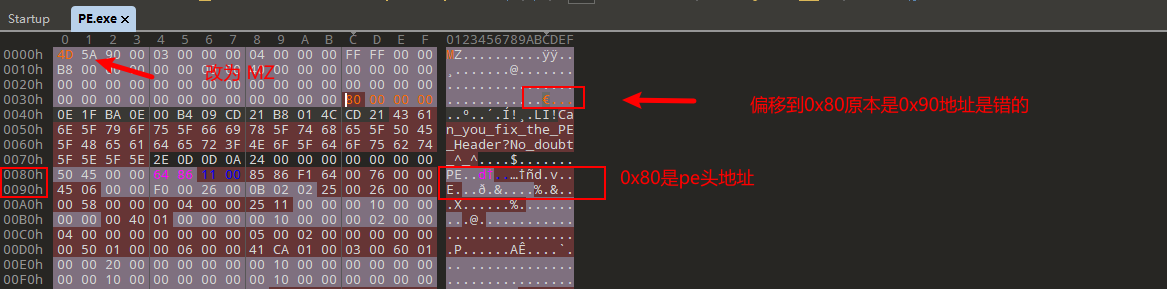
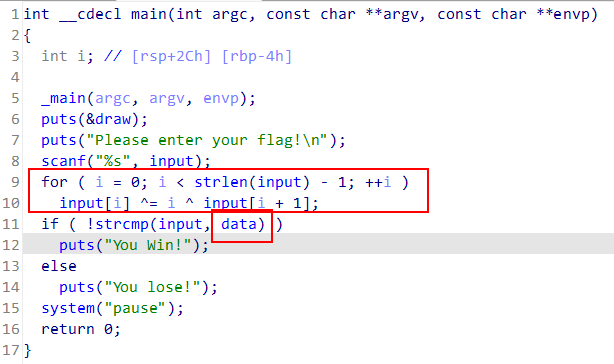
1 | |
flagflag{Y0u_kn0w_what_1s_PE_File_F0rmat}
lazy_activtiy
点购10000次就弹出flag
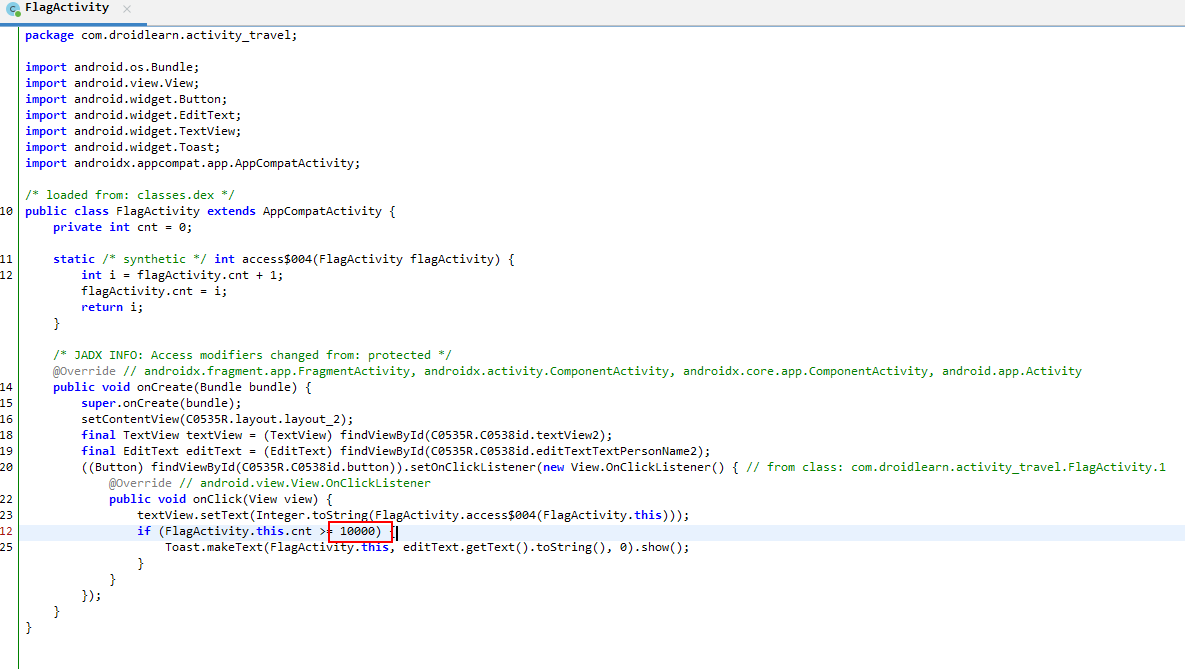
搜索flag 在
layout
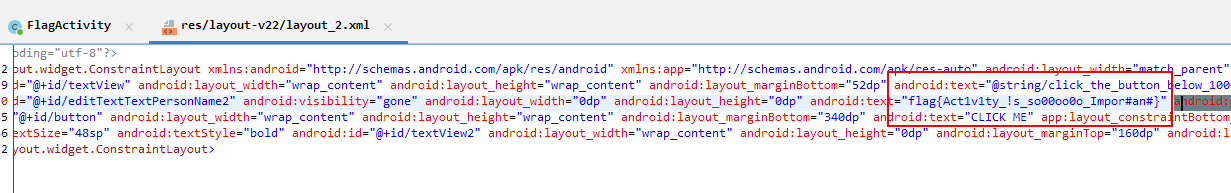
flag flag{Act1v1ty_!s_so00oo0o_Impor#an#}
New Star Ctf Week2 Re
PZthon
是python打包的
使用pyinstxtractor.py 下载/pyinstxtractor.py
python pyinstxtractor.py 文件.exe
会出来一个文件.pyc 使用pycdc 可以在下载pycdc
反编译出来
1 | |
脚本
1 | |
AndroGenshin
原神启动
方法1获取码表
先使用jadx-gui分析
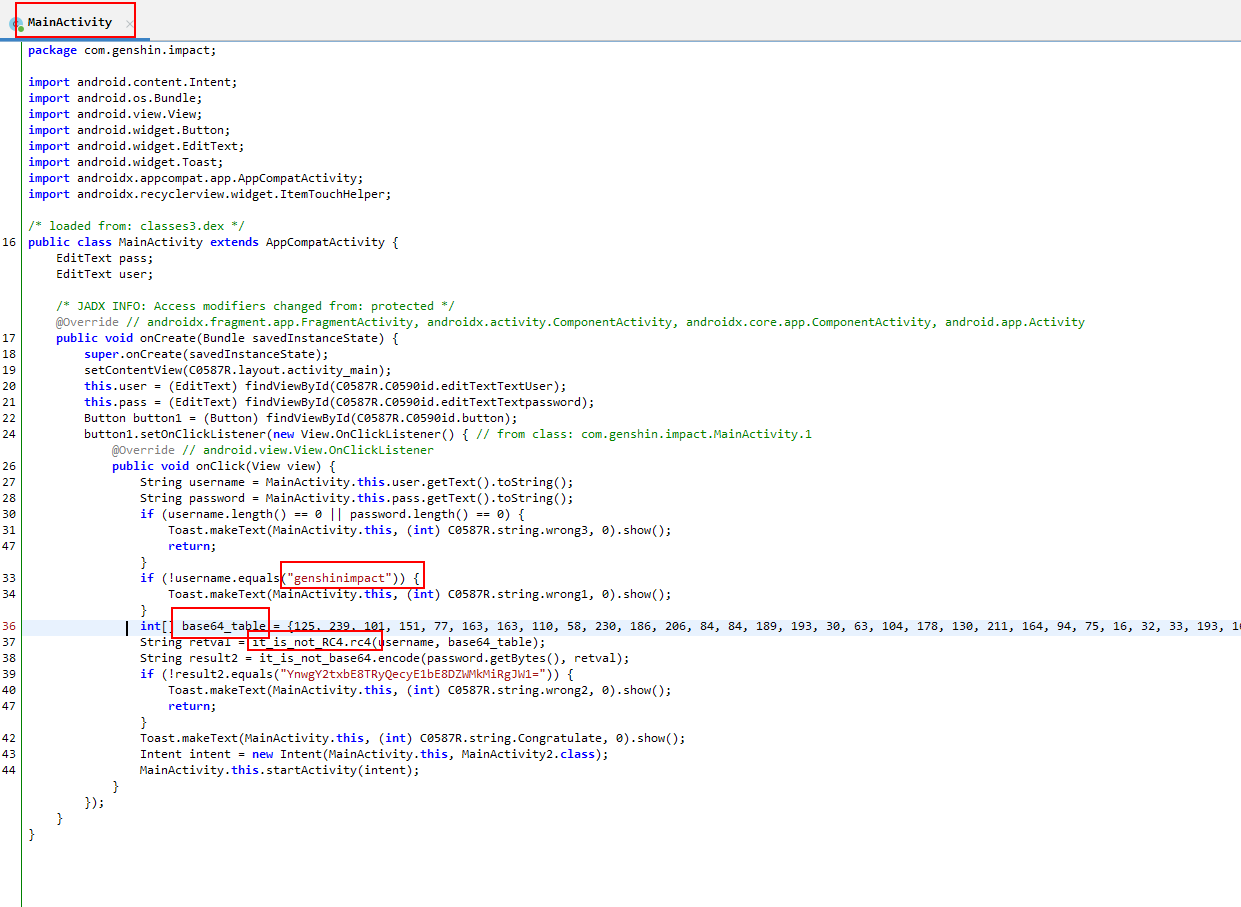
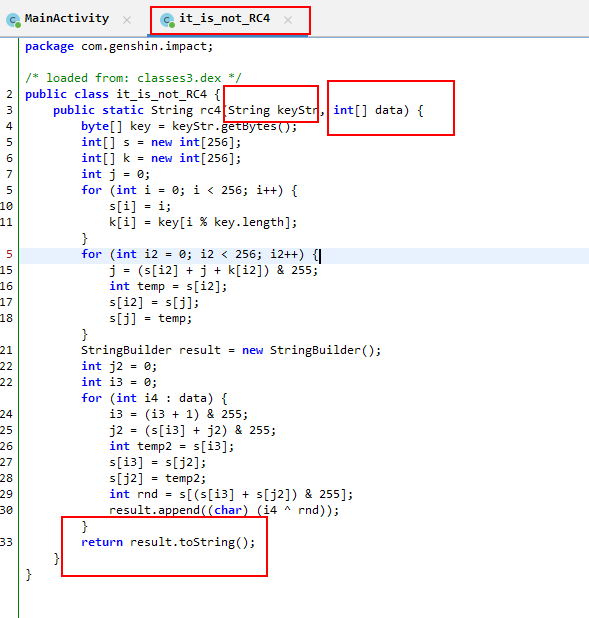
让后编写脚本
1 | |
使用frida
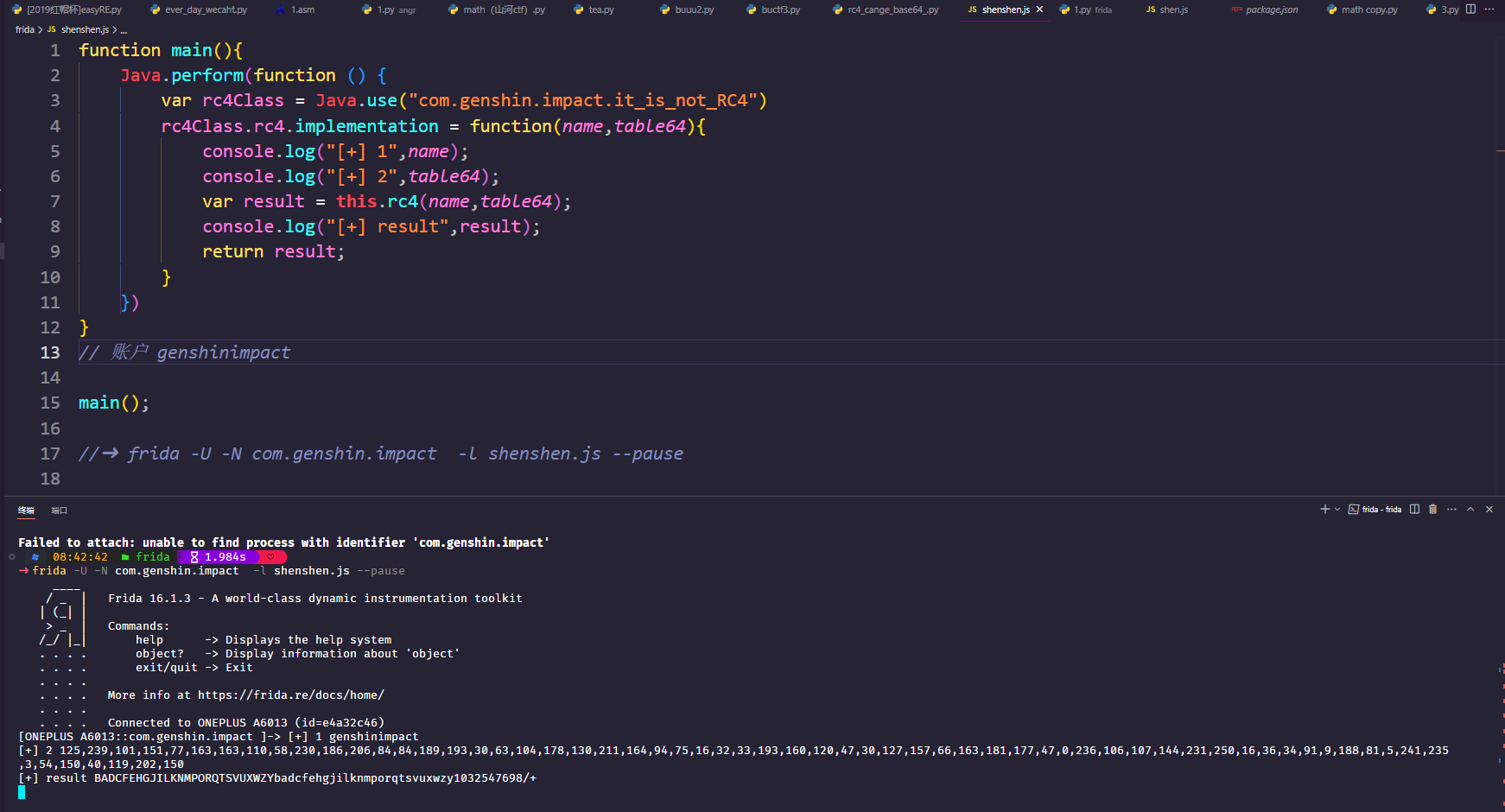
BADCFEHGJILKNMPORQTSVUXWZYbadcfehgjilknmporqtsvuxwzy1032547698/+
方法2获取码表
使用jeb调试
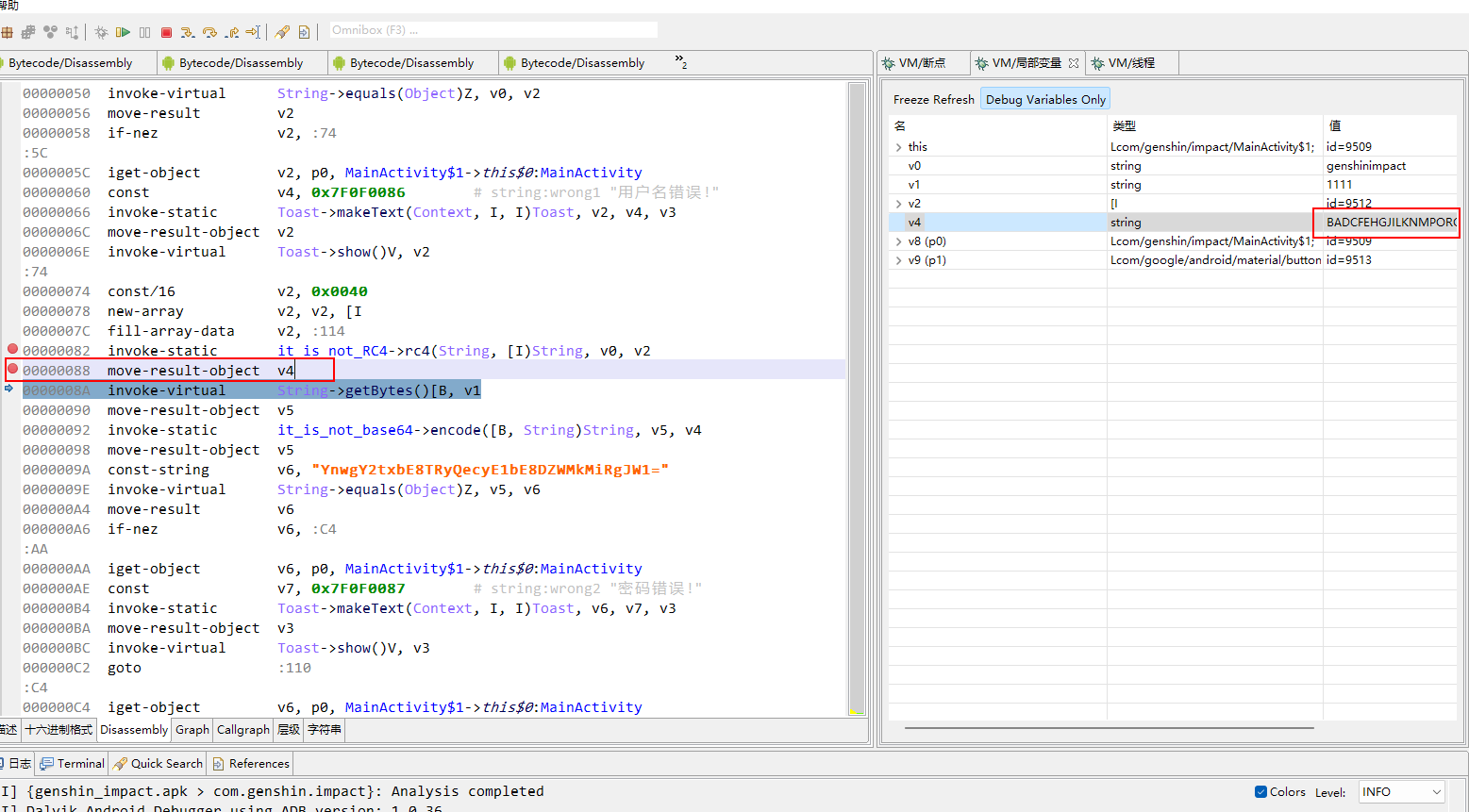
BADCFEHGJILKNMPORQTSVUXWZYbadcfehgjilknmporqtsvuxwzy1032547698/+
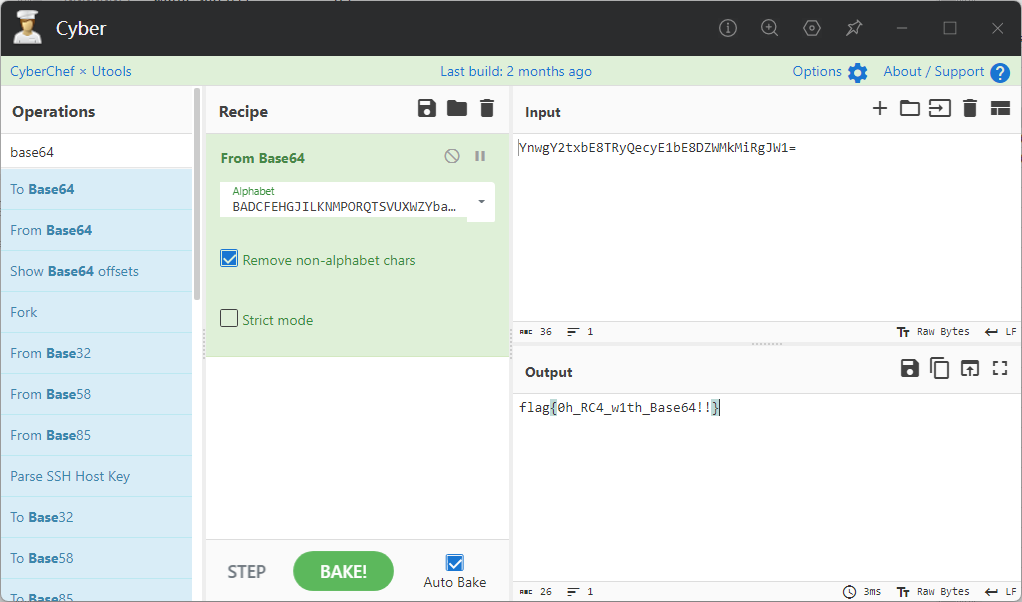
flag flag{0h_RC4_w1th_Base64!!}
SMC
看标题应该是个SMC题
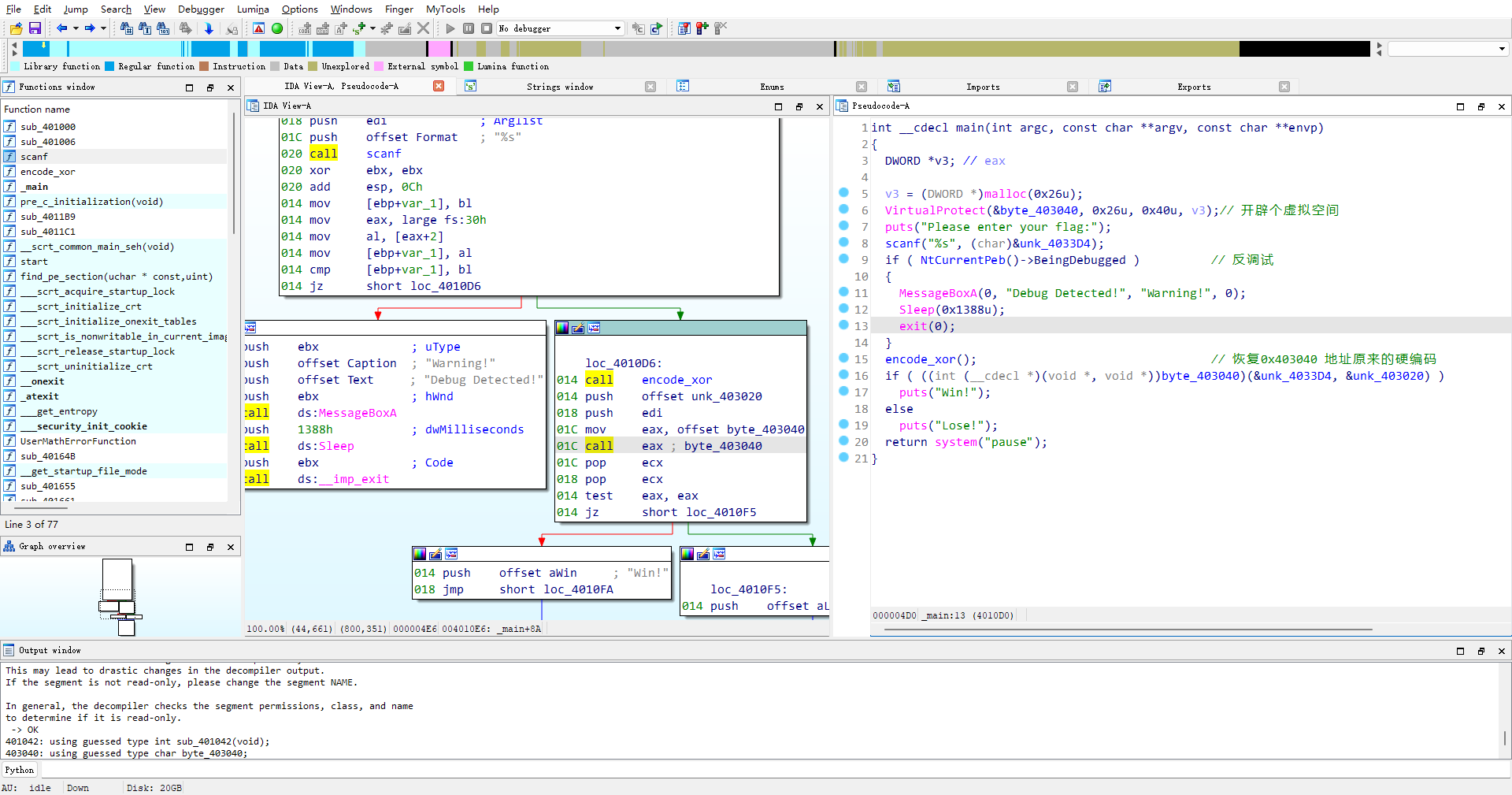
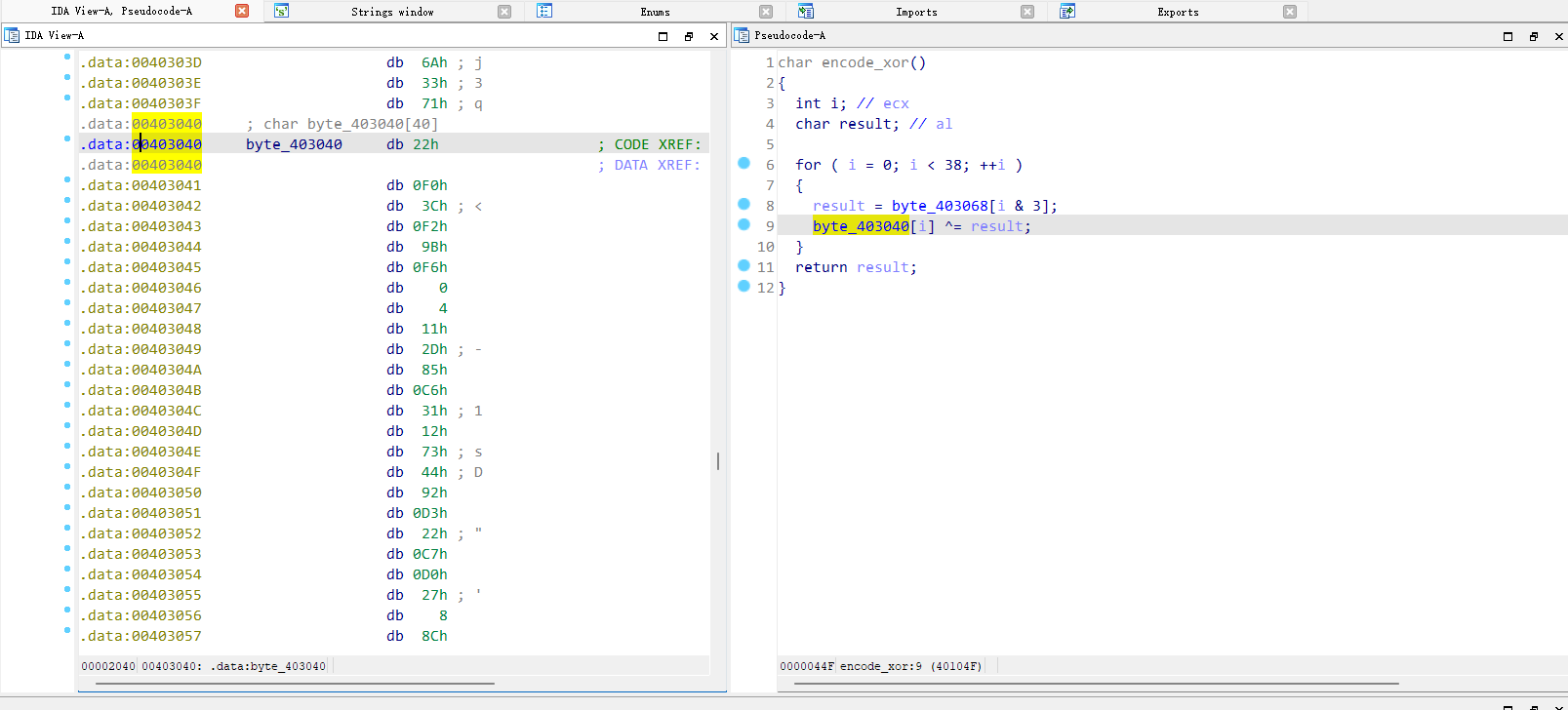
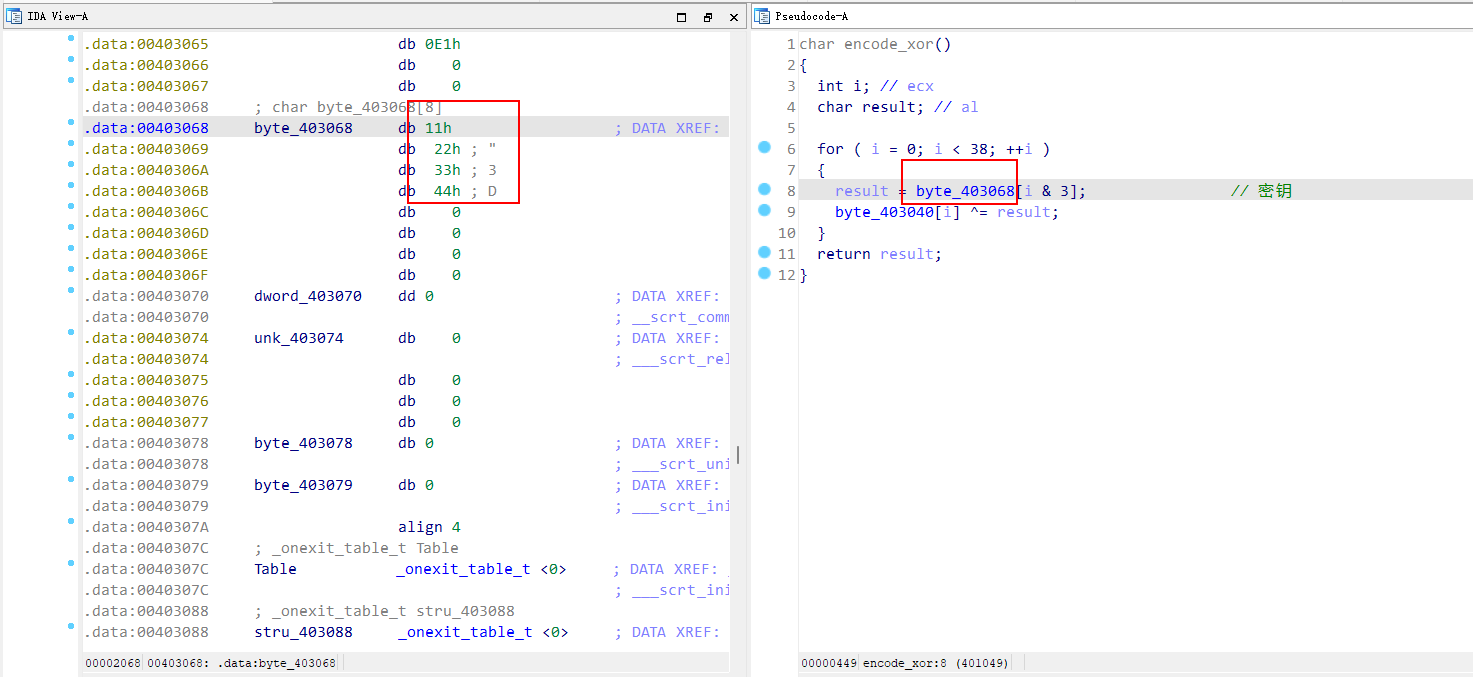
编写ipython代码
1 | |
shift+f2
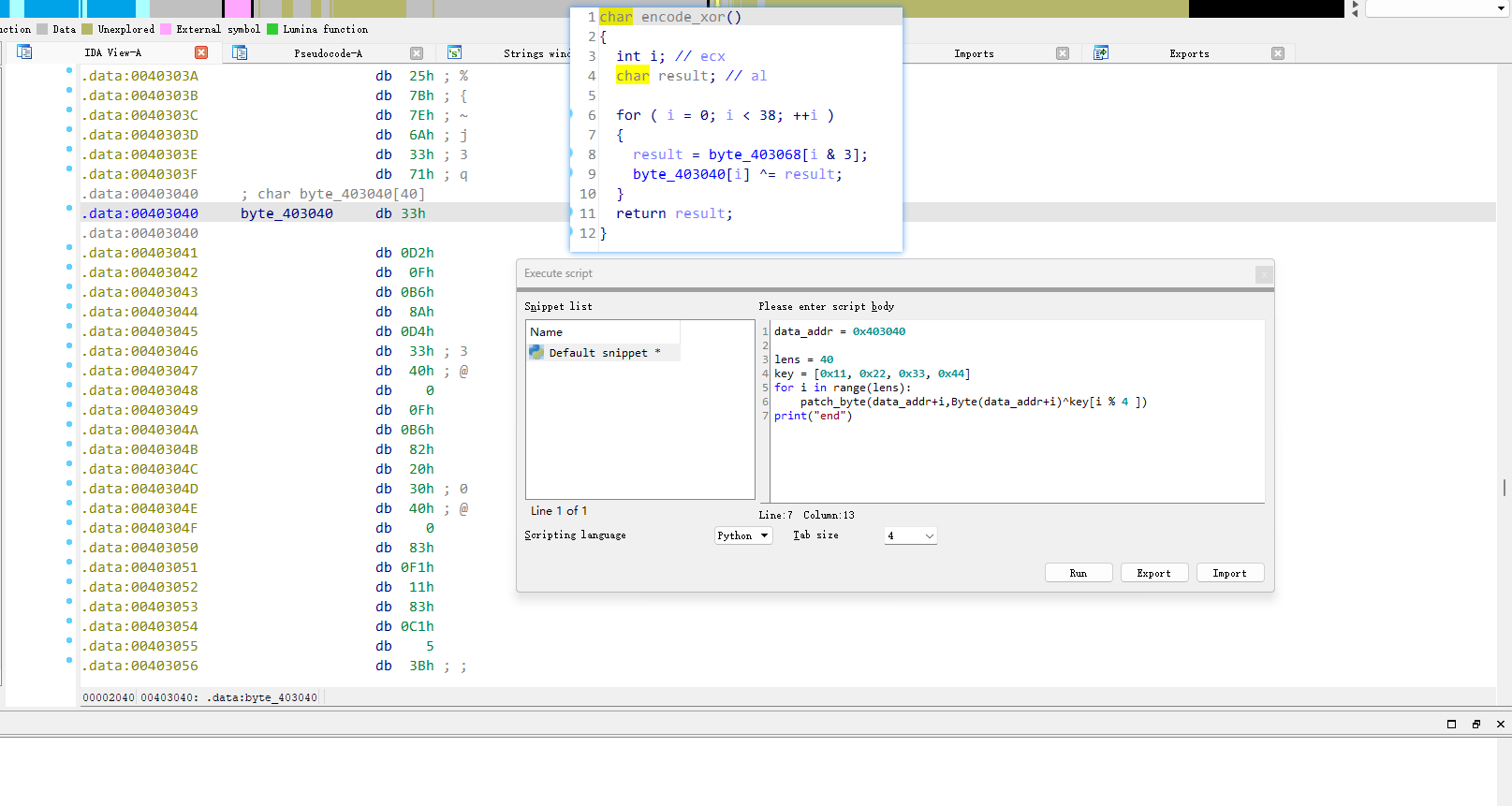
在0x403040地址下按c转换为代码按p转化为函数
进入发现操作密文编写脚本
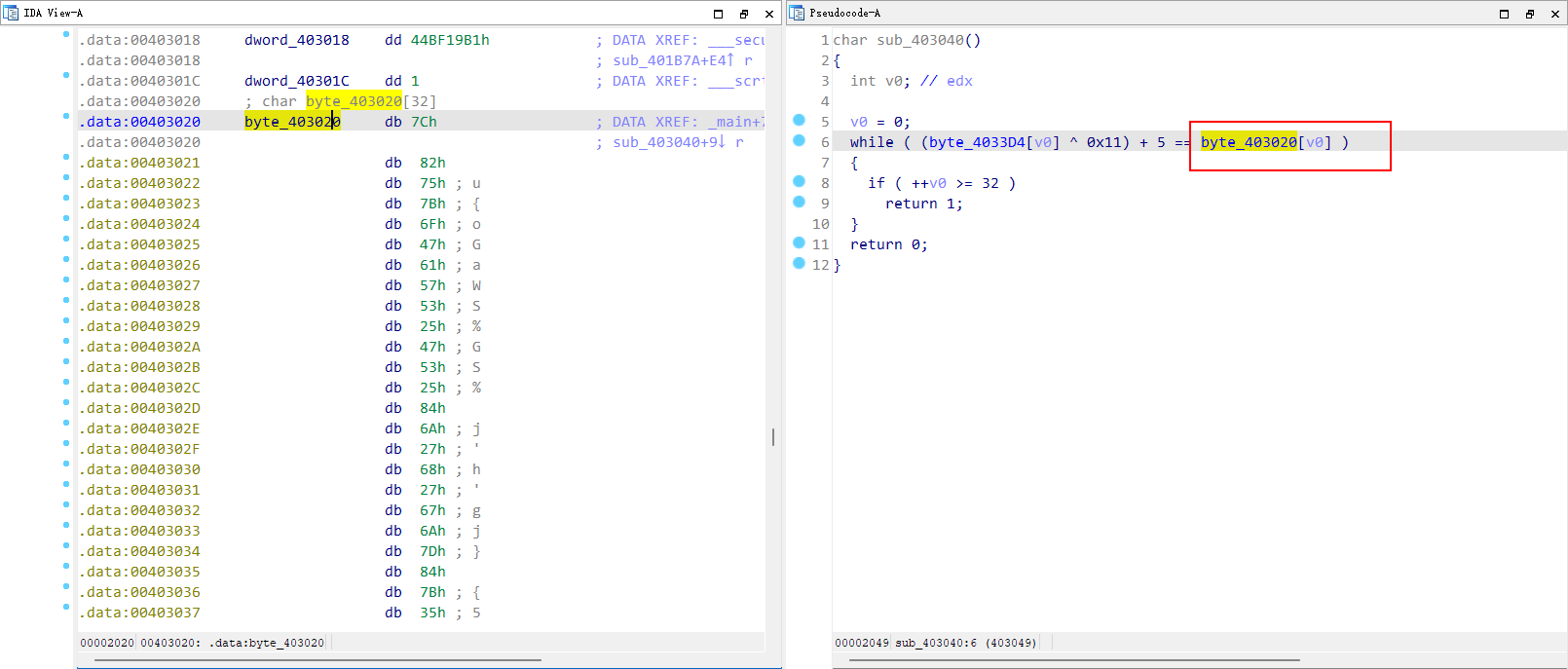
1 | |
flag flag{SMC_1S_1nt3r3sting!!R1ght?}
Petals
据题目标题应该是花指令
程序中0x00000000000013B0 地址
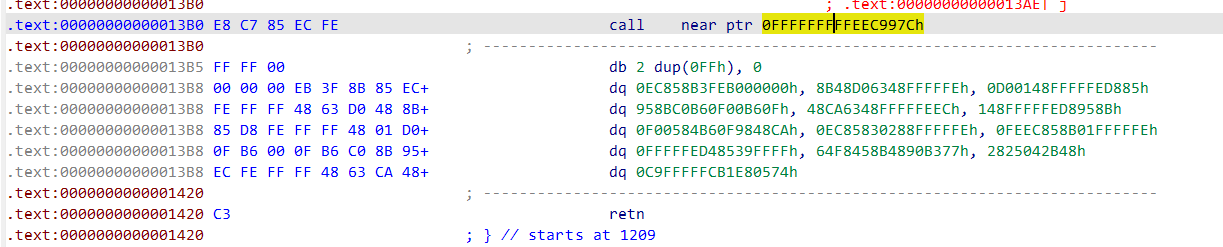
按d转换为硬编码将0xe8改为(0x90== nop)
改完u未定义在按快捷键c转换为汇编代码0x000000000000120D按p生成函数push rbp
进入伪代码
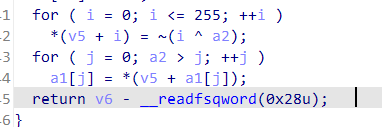
1 | |
flag flag{d780c9b2d2aa9d40010a753bc15770de}
C?C++?
die查壳发现是c#是时候是你了dnspy和ilspy
1 | |
编写脚本
1 | |
flag flag{45dg_ng78_d8b5_1a7d_gh47_kd5b}
easy_enc
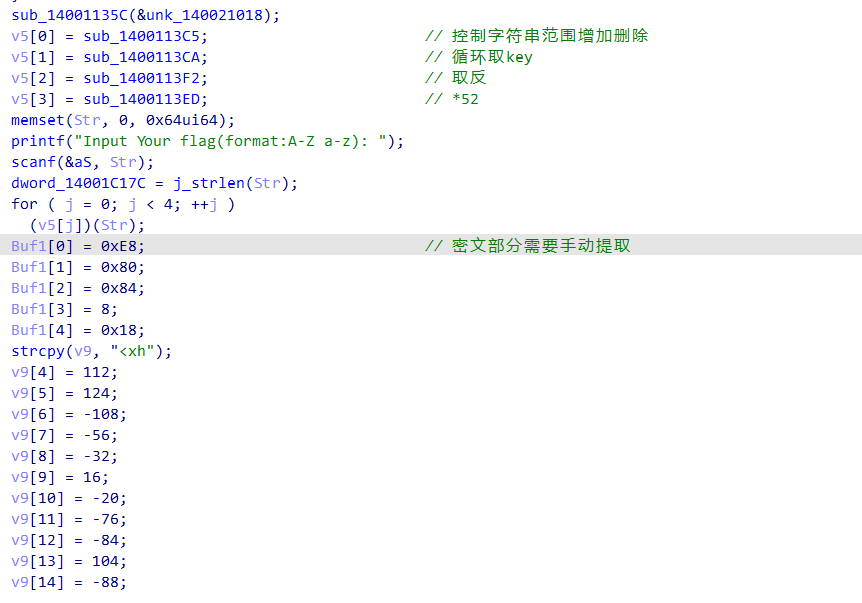
脚本
1 | |
flag flag{BruteForceIsAGoodwaytoGetFlag}
R4ndom
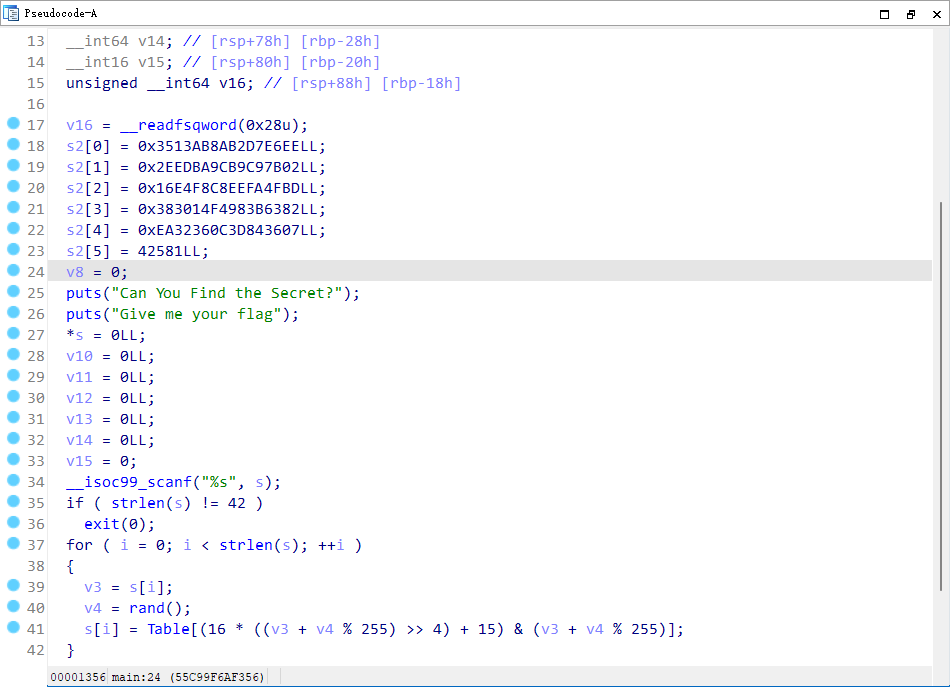
随机种子srand 0x5377654E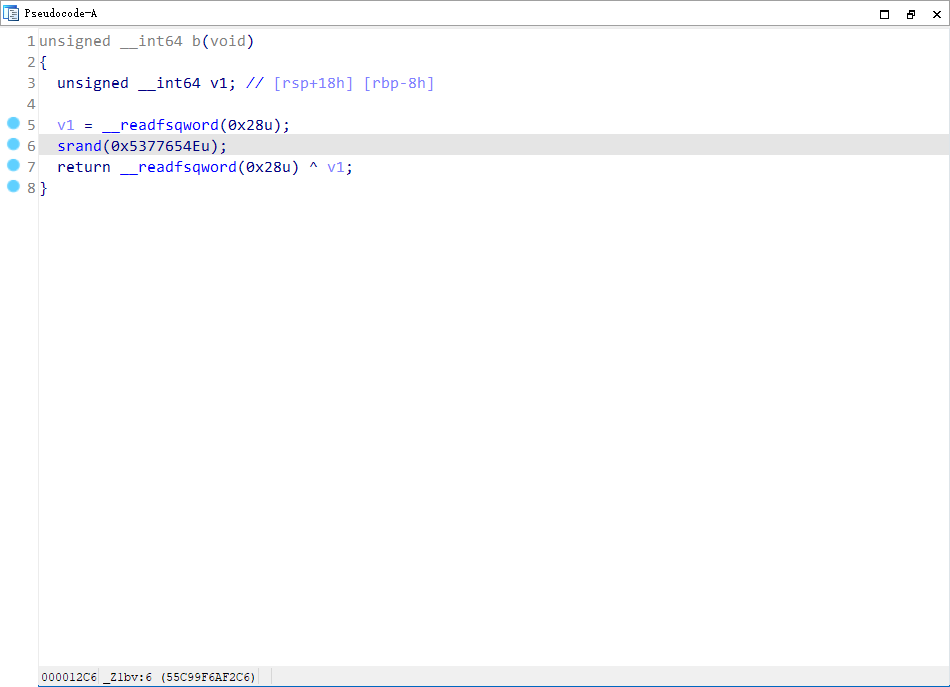
处理大小端序
1 | |
一
编写代码注意用Linux运行
记录点Linux和Windows 的rand随机数不同记使用对应的系统编译
1 | |
flag flag{B8452786-DD8E-f12C-E355-2B6F27DA25F9}
二
1 | |
flag flag{B8452786-DD8E-f12C-E355-2B6F27DA25F9}
AndroDbgMe
使用jeb调试就弹出flag了
flagflag{Let_1t_run_@t_f1rs7_m@ybe_th3_b3st}
官方解法:
考点:Java层动调
flag:flag{Let_1t_run_@t_f1rs7_m@ybe_th3_b3st}
解题步骤
本题调试即可以得到Flag
关于如何调试apk进程,需要在Manifest需要给AndroidManifest.xml设置
android:debuggable="true"
使用apktool 工具解包修改manifest
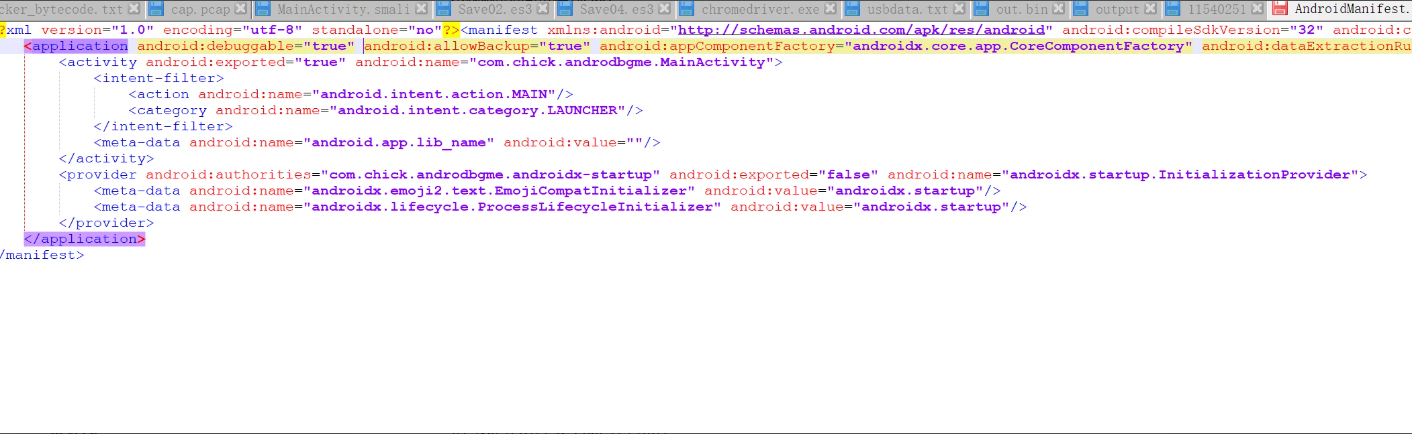
重打包回去之后进行签名
先对文件进行对齐
zipalign -p -f -v 4 input.apk output_unsigned.apk
加签名 其中abc.keystore 是我通过androidstudio生成的签名文件
也可以自行用工具生成,不再赘述
APK反编译、重打包、签名之apktool实现_apktool反编译还是乱码-CSDN博客
apksigner sign –ks abc.keystore output_unsigned.apk
安装到手机上,以调试模式启动
adb shell am start -D -n com.chick.androdbgme/.MainActivity
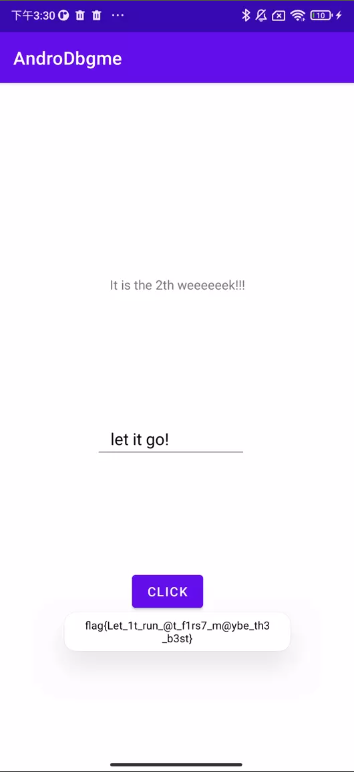
用jeb attach上去,得到flag