buuctf&&RE&&前12道题 本文章用到的工具
die下载地址 :https://github.com/horsicq/DIE-engine/releases
exeinfo下载地址 : https://github.com/ExeinfoASL/ASL/blob/master/exeinfope.zip
idapro下载地址:https://www.123pan.com/s/mCY8Vv-q4hWd.html
jadx-gui 下载地址 https://github.com/skylot/jadx/releases/tag/v1.4.6
apkidc下载地址:https://down.52pojie.cn/?query=apkid
仅用于学习
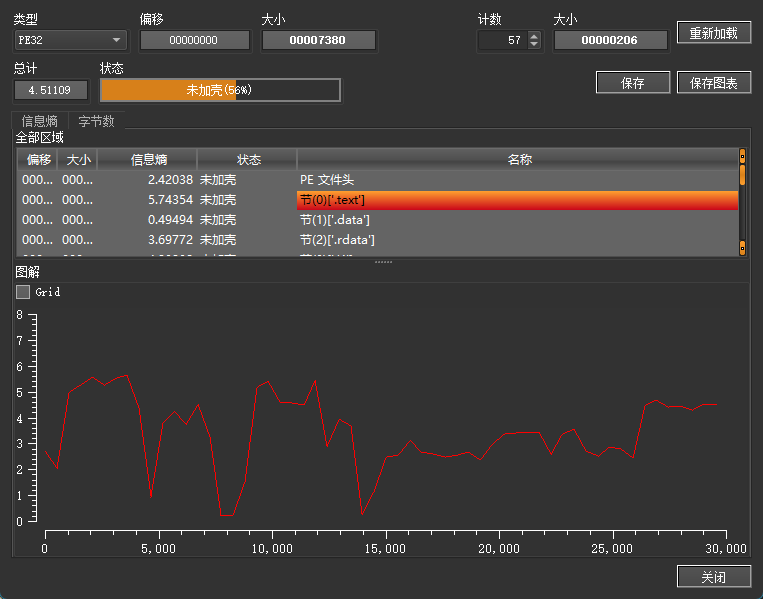
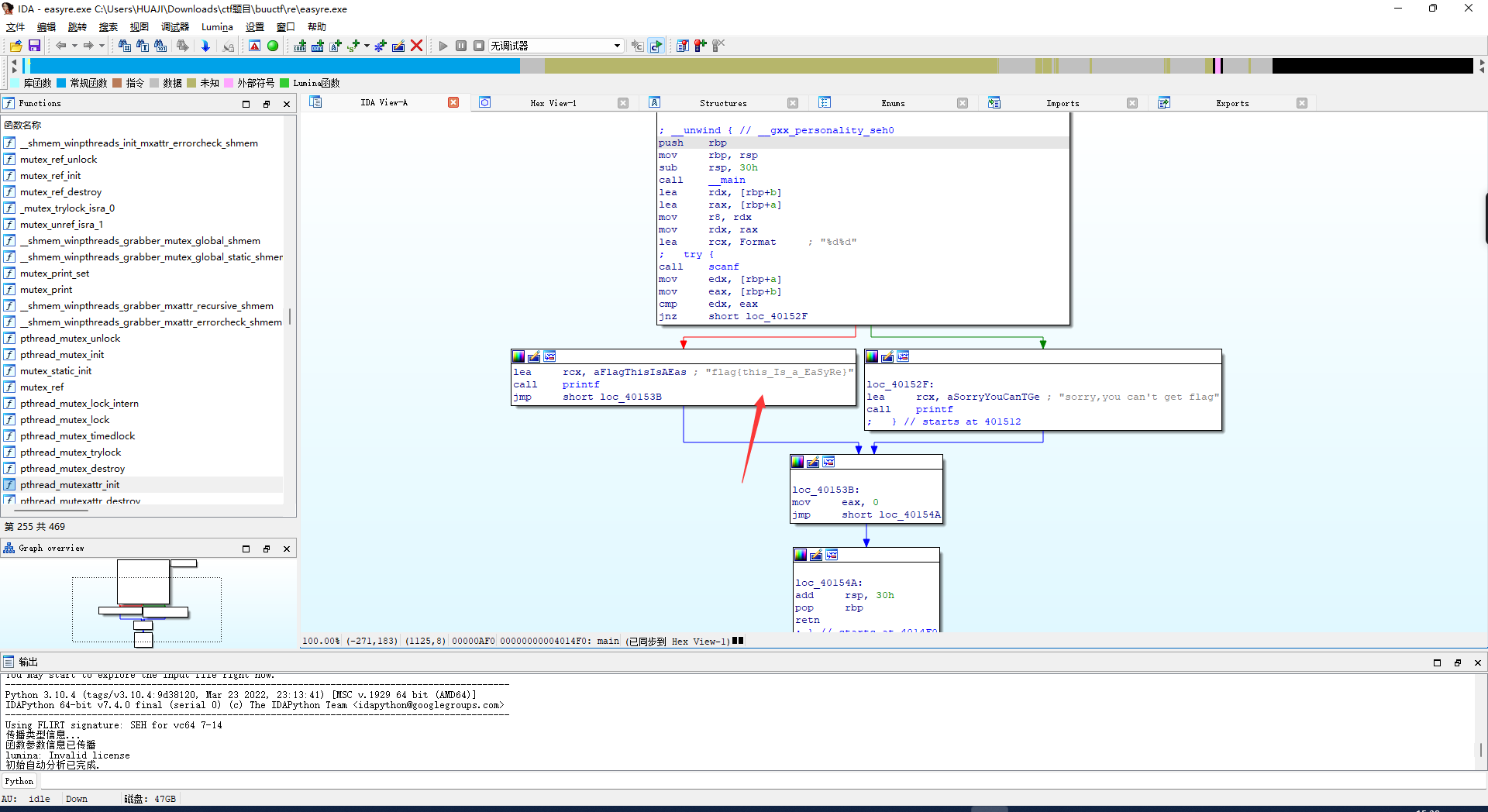
easyre 用die分析一下
使用ida64打开easyre.exe
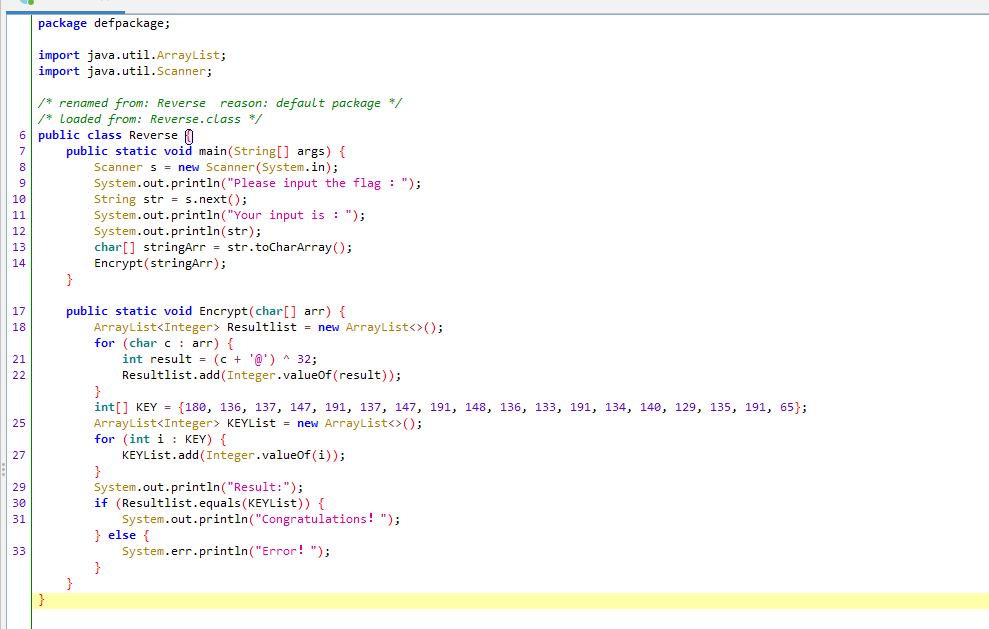
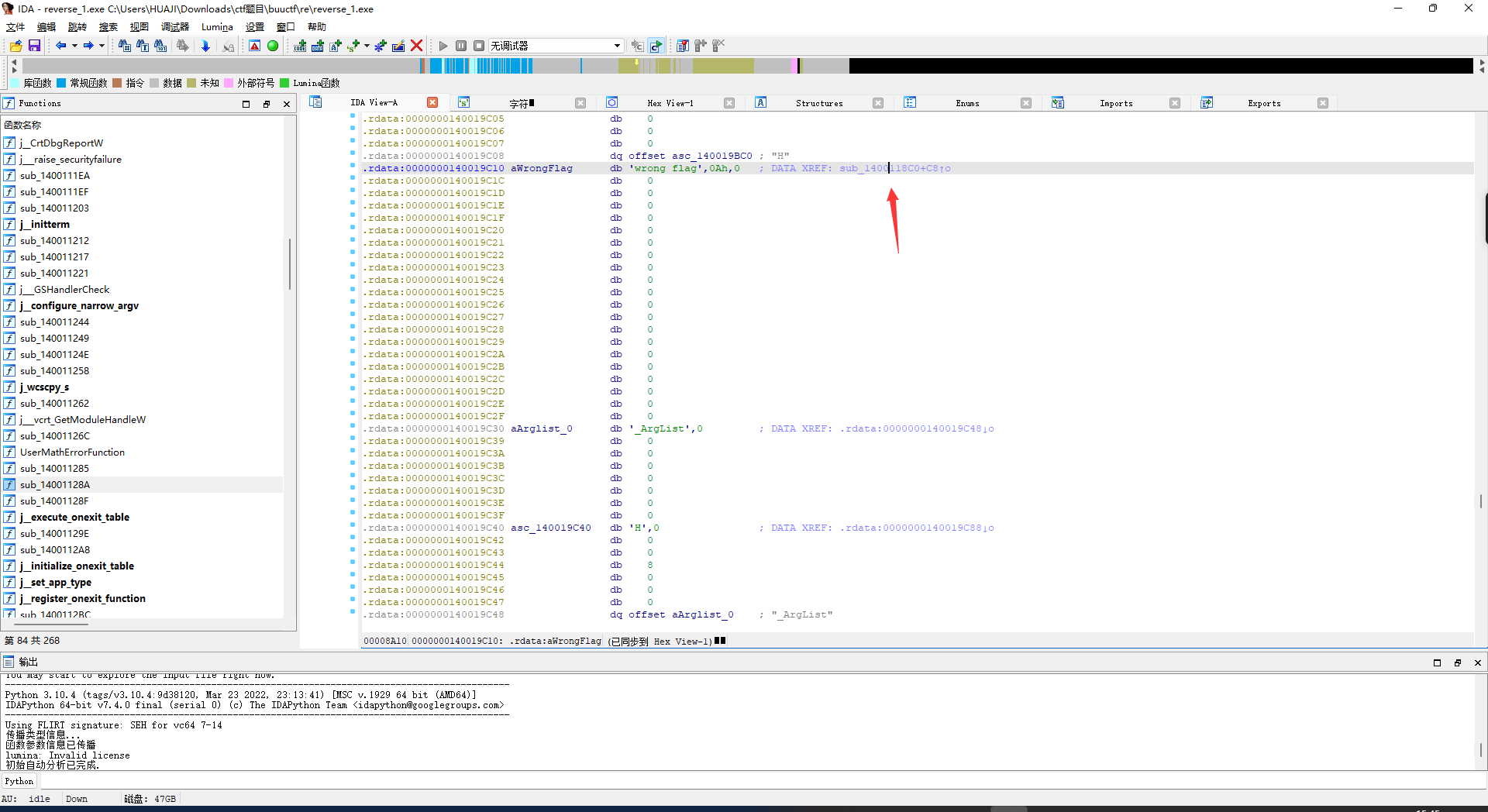
reverse1
shift+f12
异或
双击进入
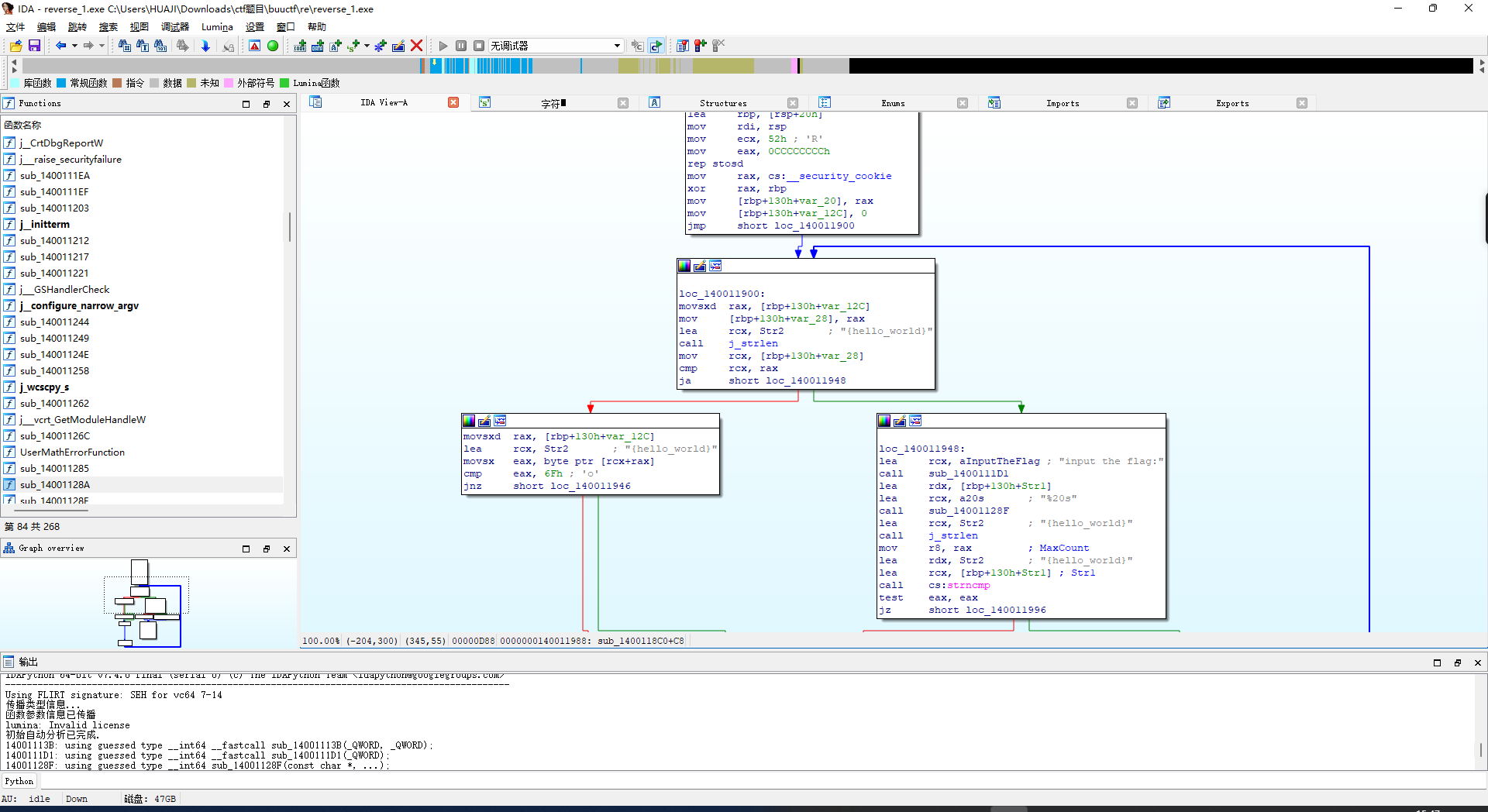
可以看到 lea 取 rcx str2 为 {hello_world}
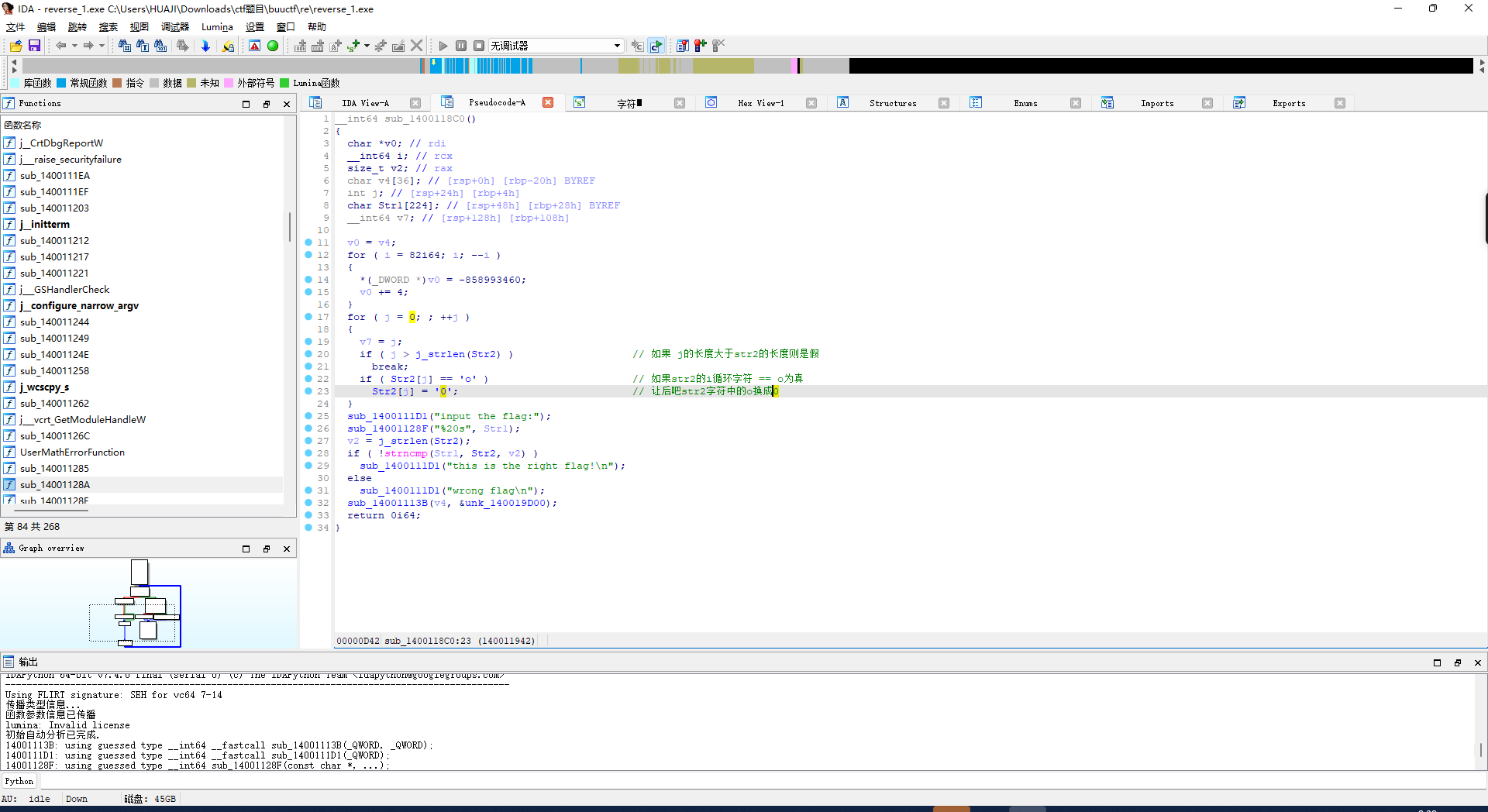
让后f5反编译查看伪代码
将:{hello_world}
替换o为0
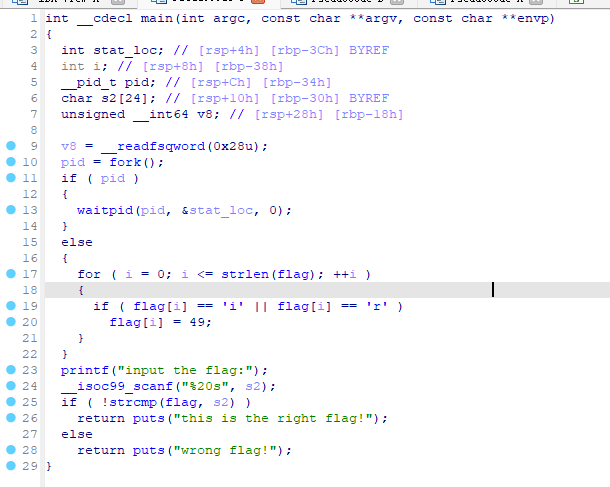
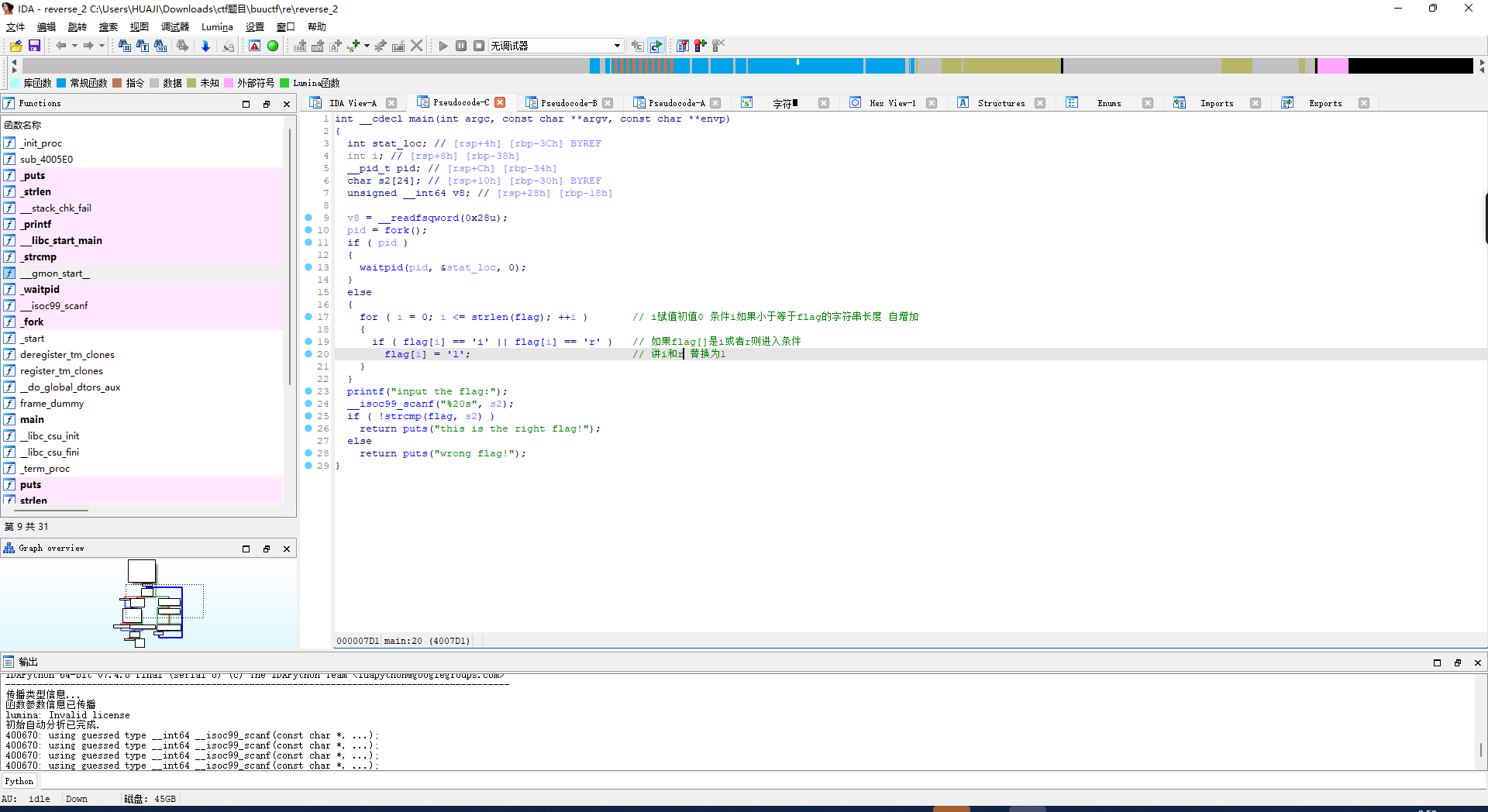
reverse2
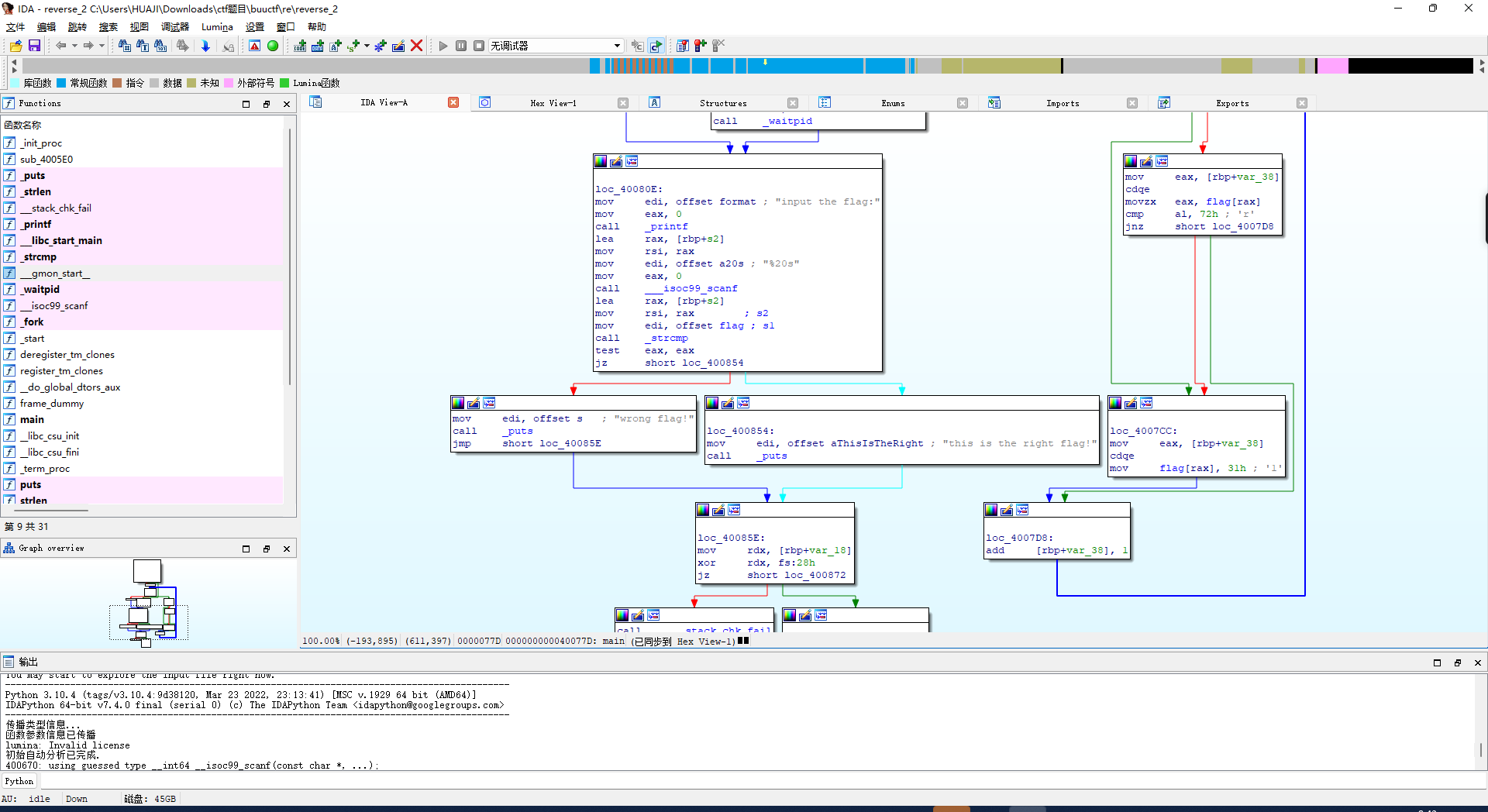
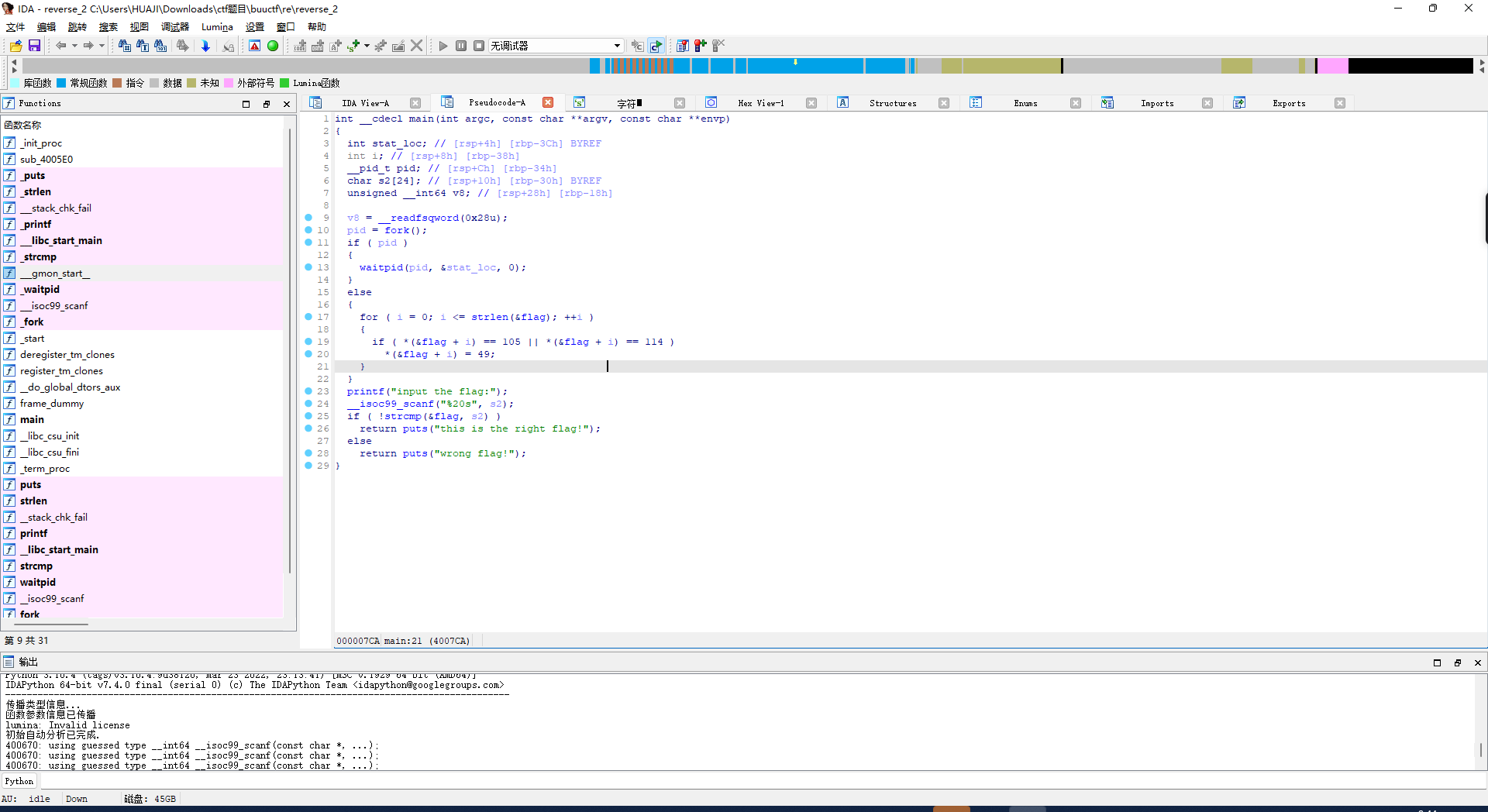
直接f5反编译
让后shift+f12
暂时存储一下
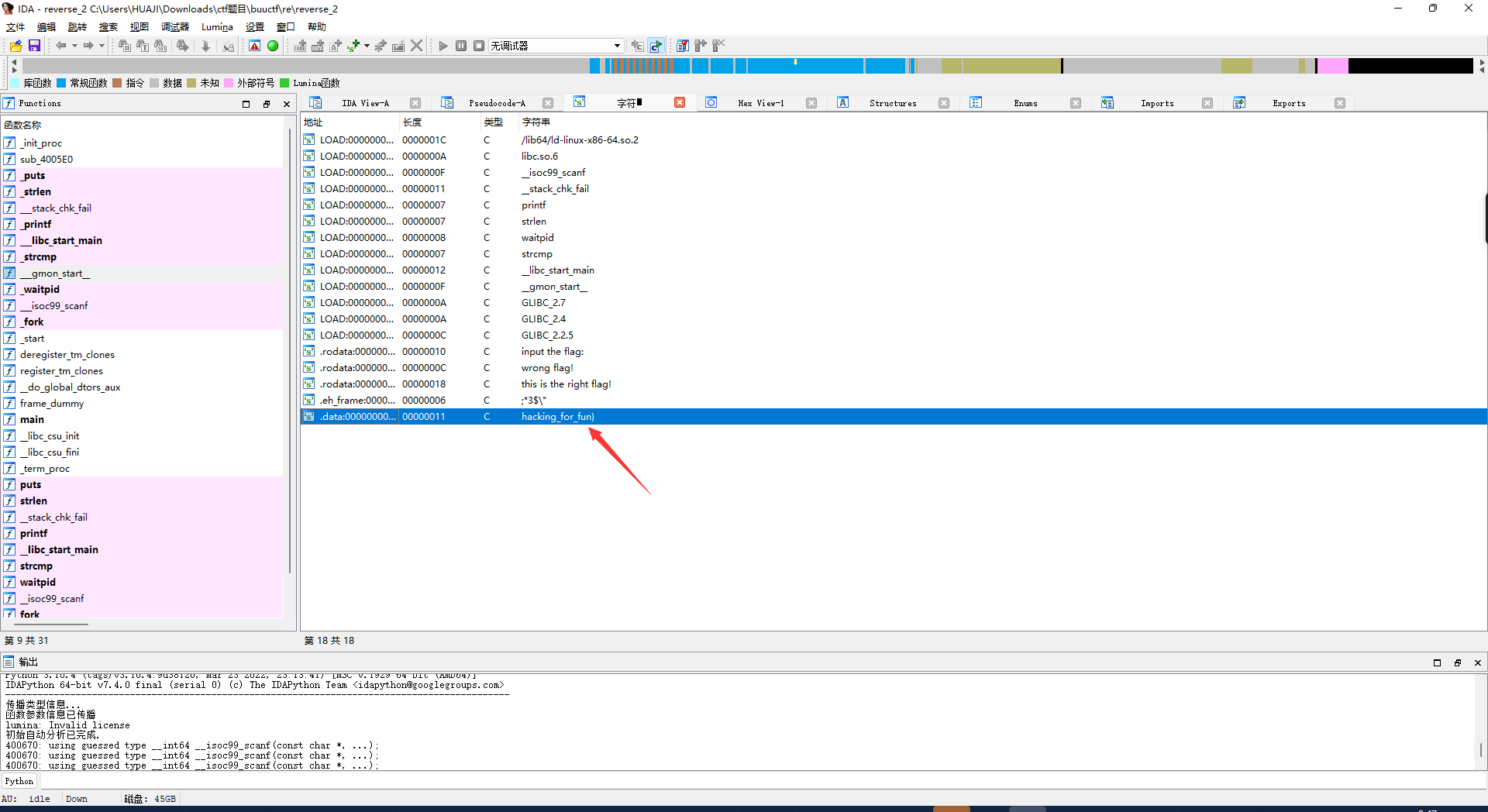
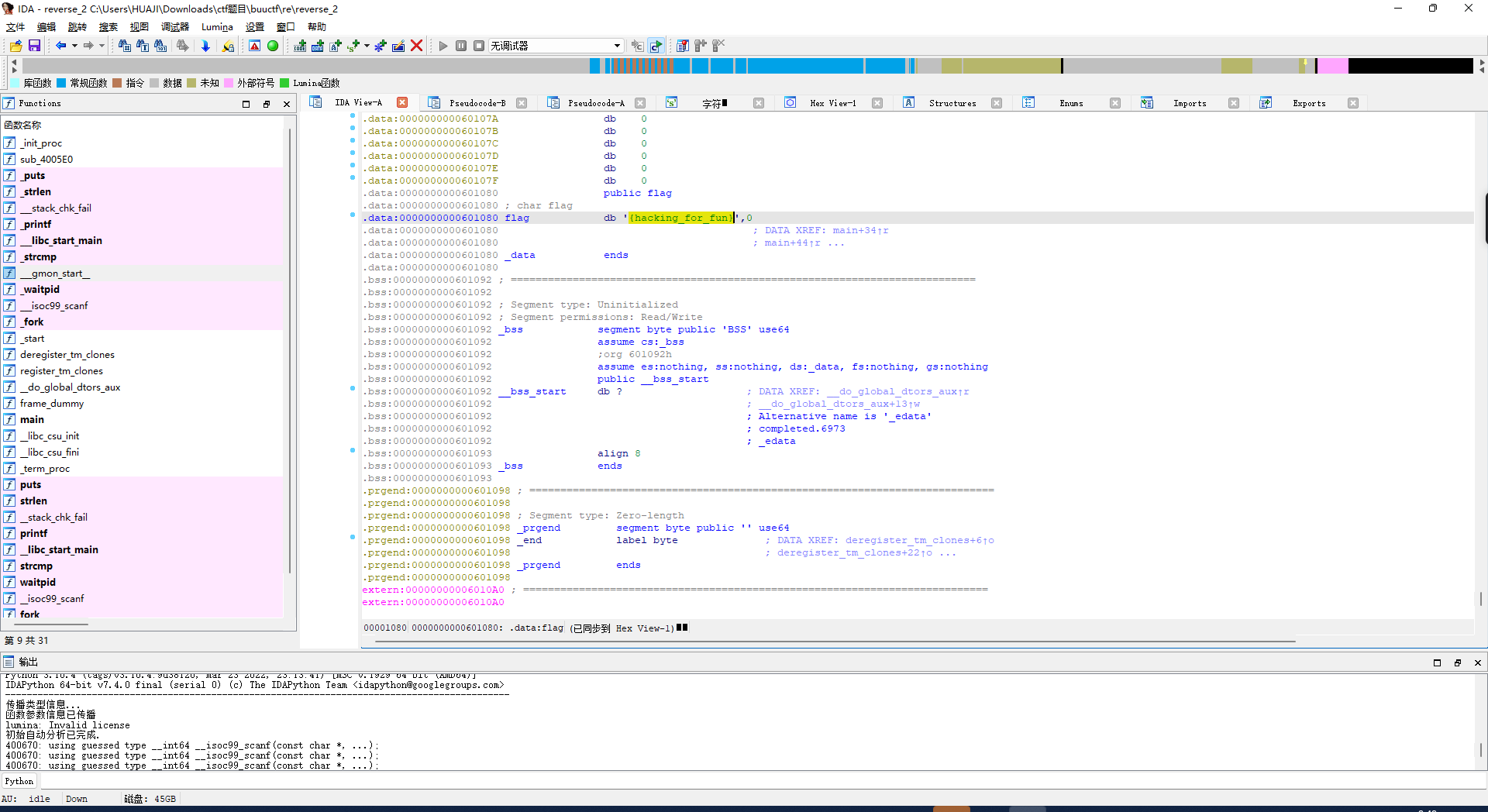
将 eax 取内存 {hacking_for_fun}
返回看到
eax, byte ptr flag[rax]
回到刚刚反编译的伪代码
将 :{hacking_for_fun}
i和r替换为1
内涵的软件
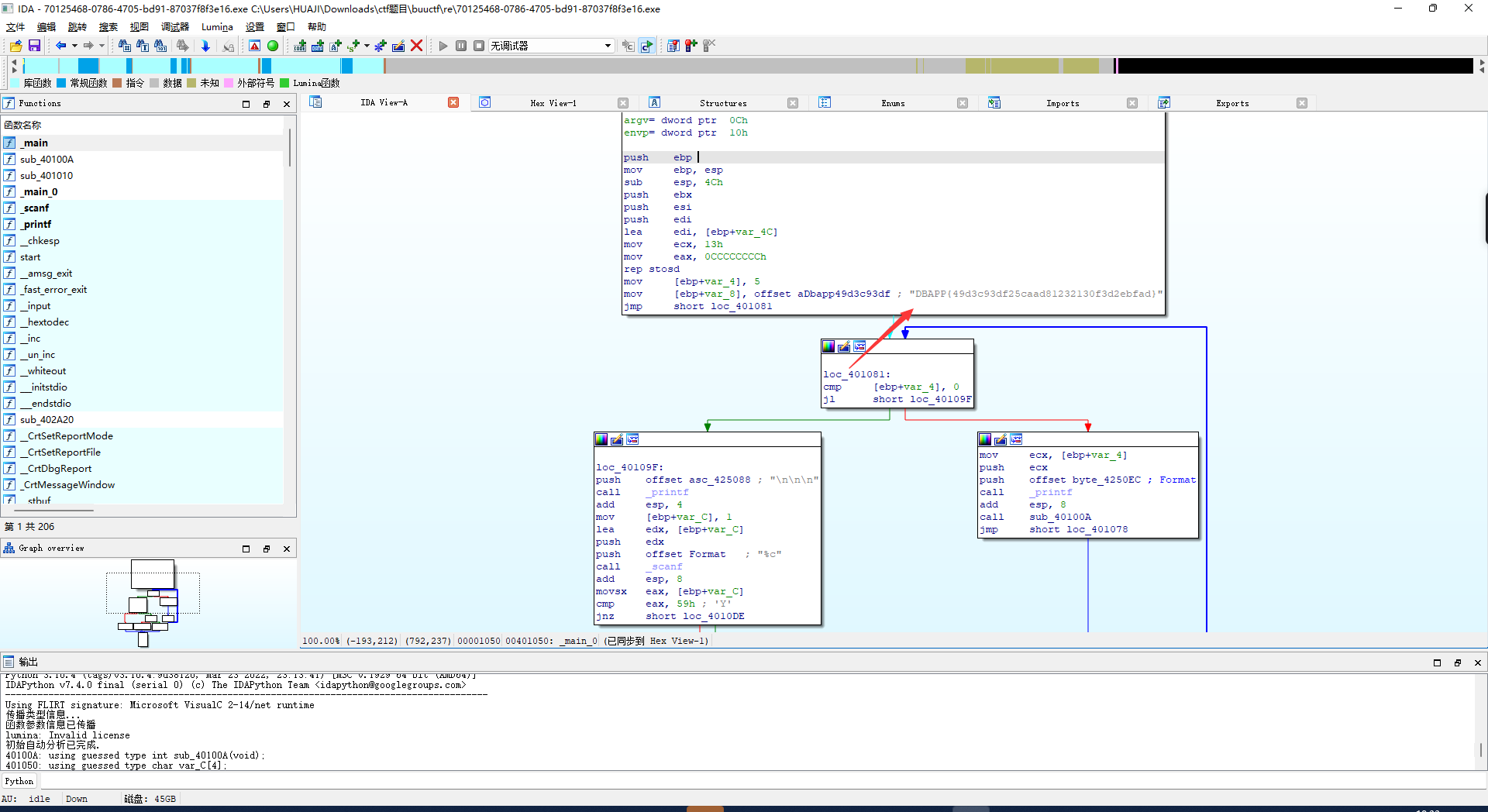
双击进入main_0
直接flag
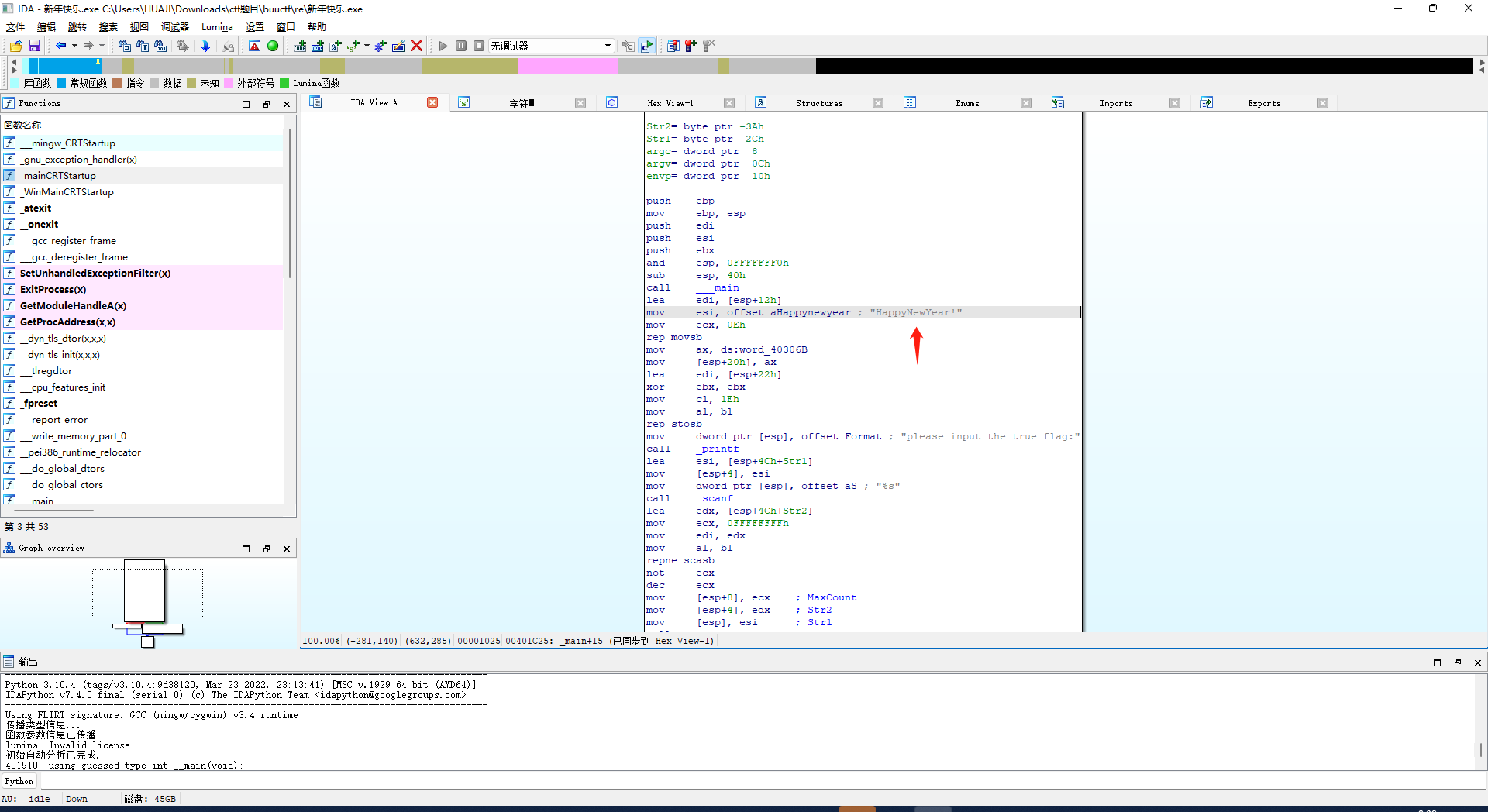
新年快乐
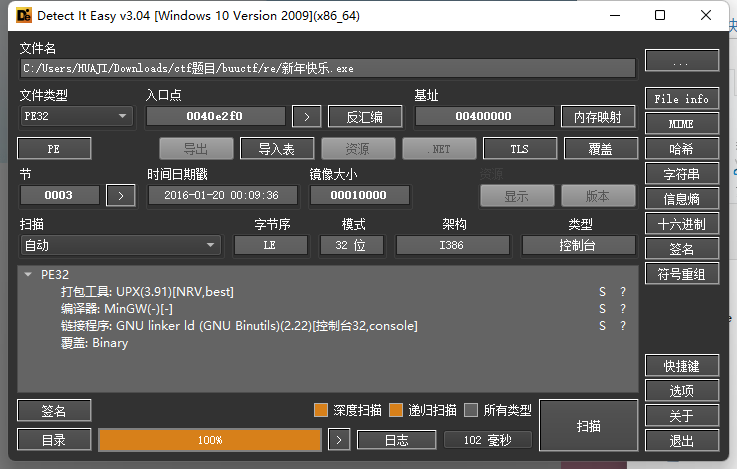
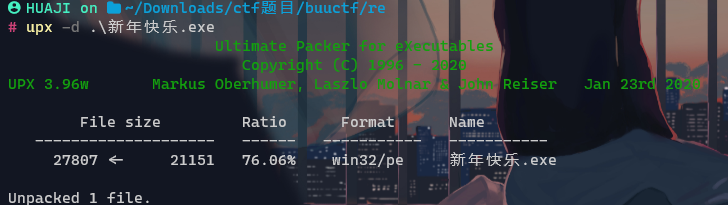
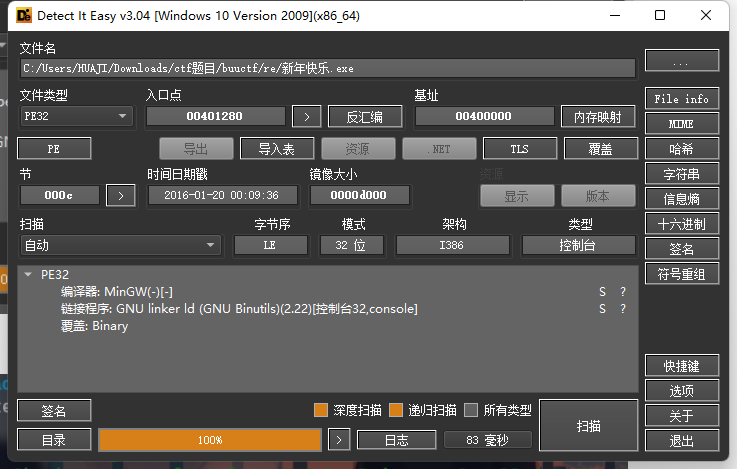
upx加密使用工具去壳 or 动态od 脱壳
idapro32打开就是flag
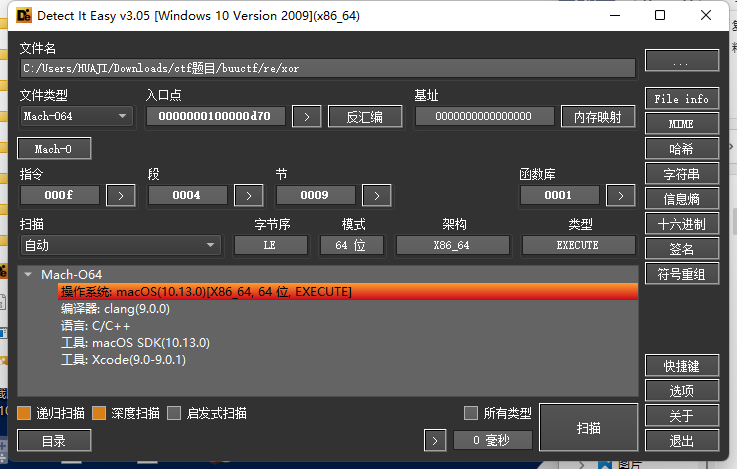
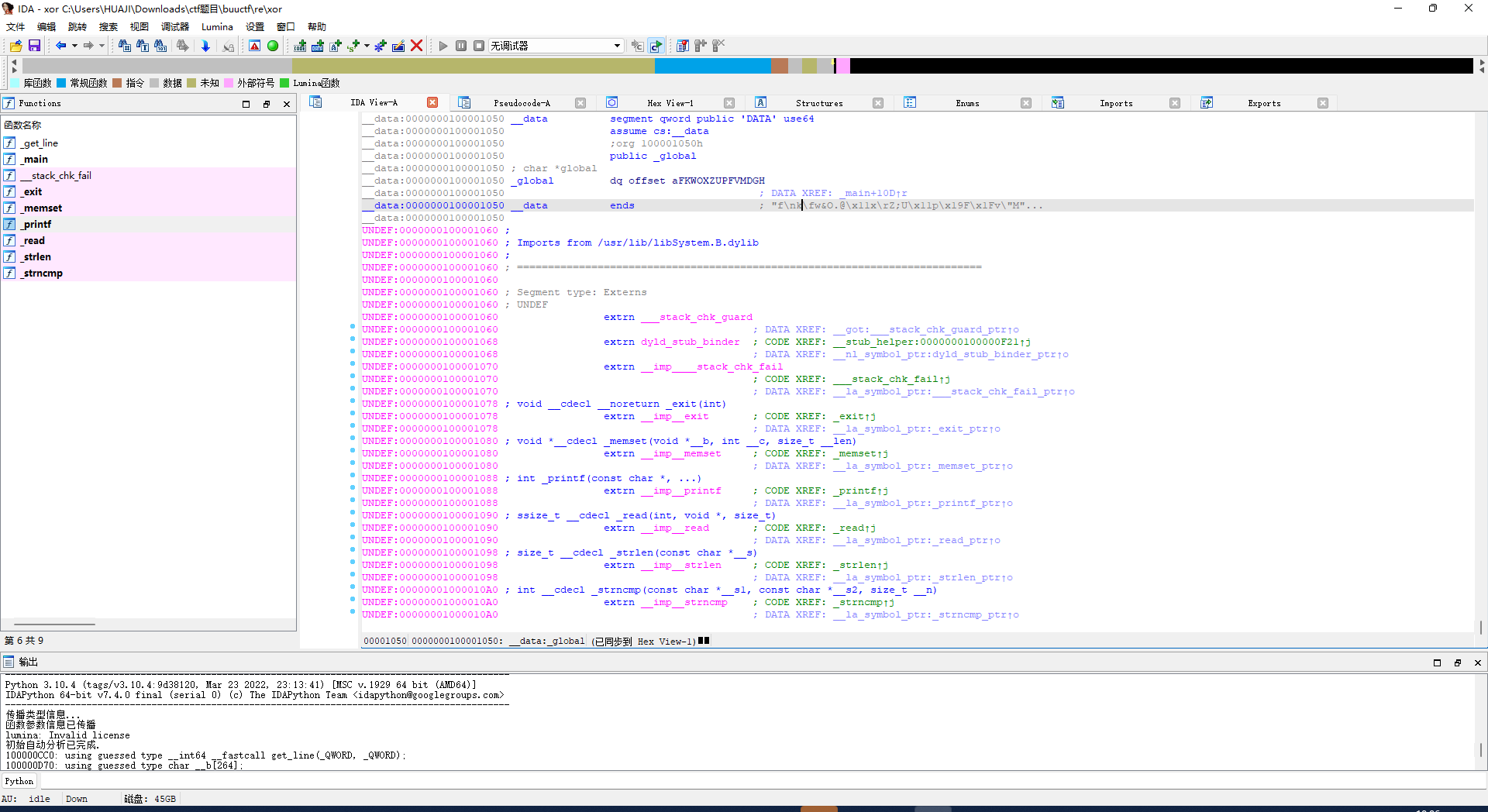
xor
无壳64位mac 软件 ida64pro打开直接f5反编译
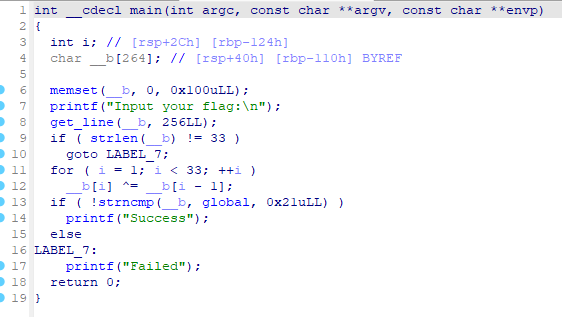
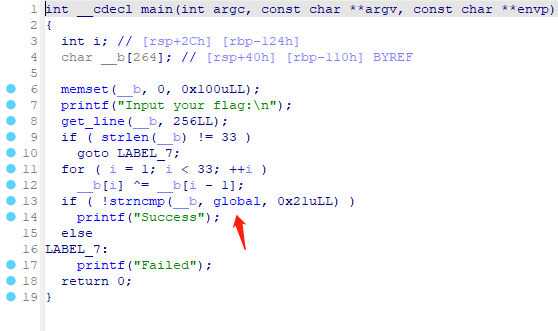
双金进入global
双击进入里面
让后shift+e
转换为数组
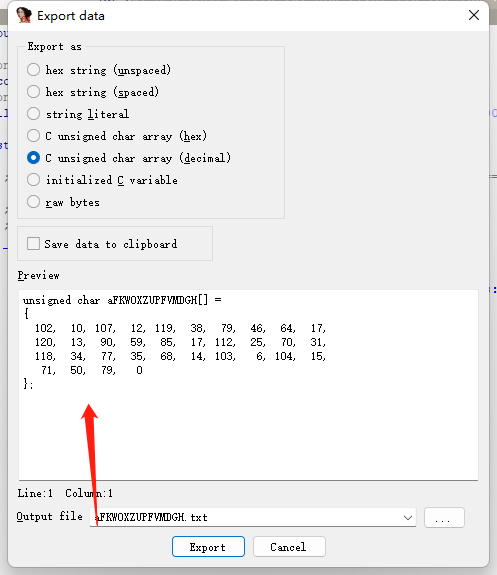
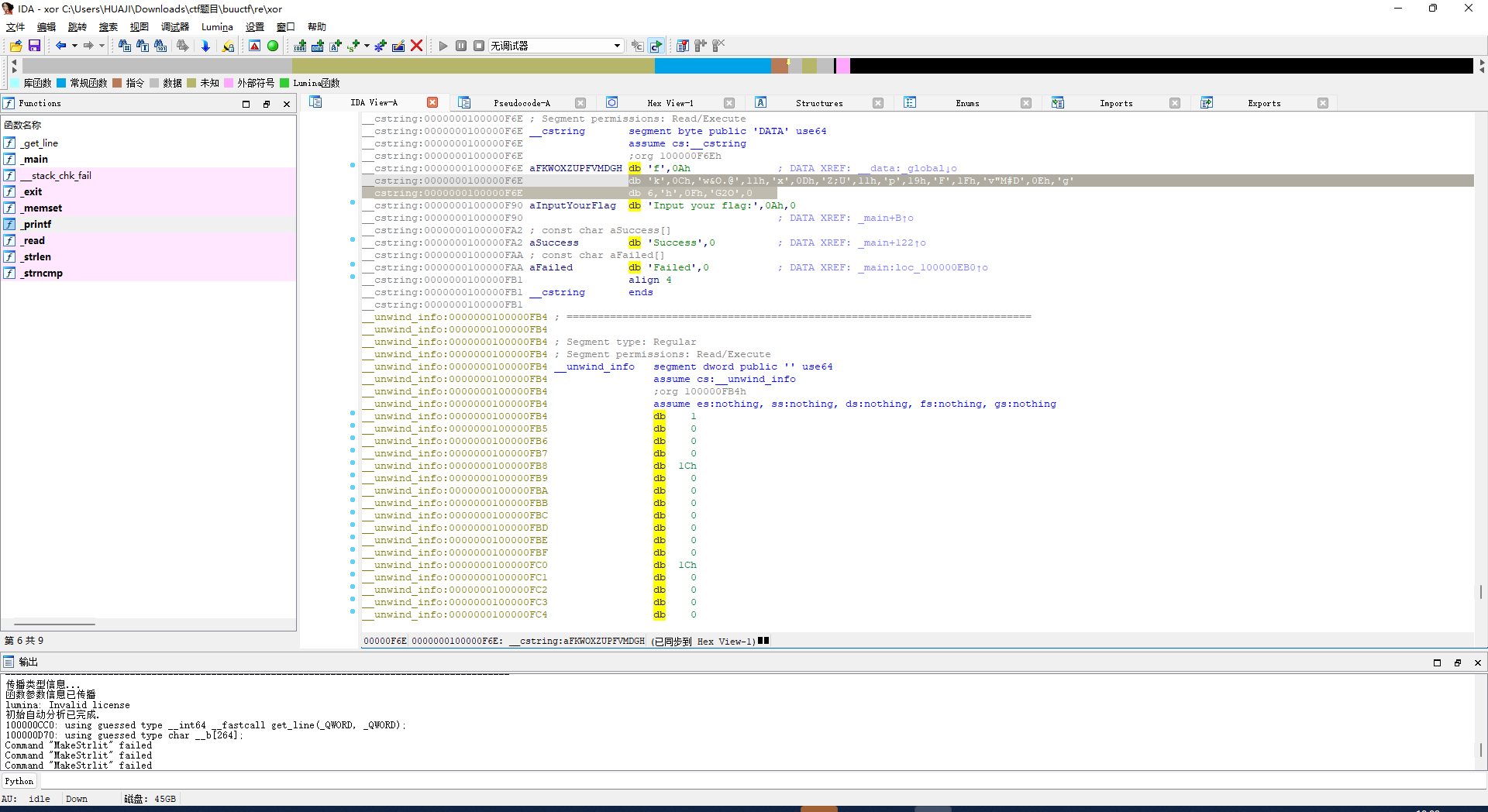
密文[0x66, 0x0A, 0x6B, 0x0C, 0x77, 0x26, 0x4F, 0x2E, 0x40, 0x11, 0x78, 0x0D, 0x5A, 0x3B, 0x55, 0x11, 0x70, 0x19, 0x46, 0x1F, 0x76, 0x22, 0x4D, 0x23, 0x44, 0x0E, 0x67, 0x06, 0x68, 0x0F, 0x47, 0x32, 0x4F, 0x00]
xor异或 密文 依次-1让后得到flag
1 2 3 4 5 6 7 8 cipher = [0x66, 0x0A, 0x6B, 0x0C, 0x77, 0x26, 0x4F, 0x2E, 0x40, 0x11, 0x78, 0x0D, 0x5A, 0x3B, 0x55, 0x11, 0x70, 0x19, 0x46, 0x1F, 0x76, 0x22, 0x4D, 0x23, 0x44, 0x0E, 0x67, 0x06, 0x68, 0x0F, 0x47, 0x32, 0x4F, 0x00] [0] *len (cipher)'' for i in range (1 ,len (cipher) -1 ):chr (cipher[i] ^ cipher[i-1] )print (chr(cipher[0 ])
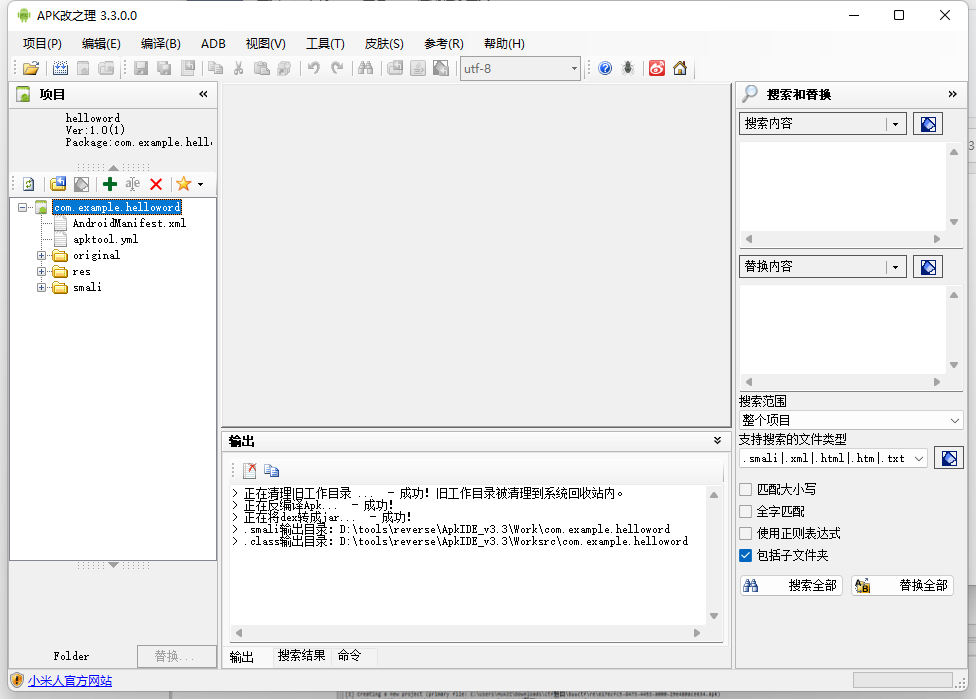
helloword 下载下来是个apk使用apkide打开
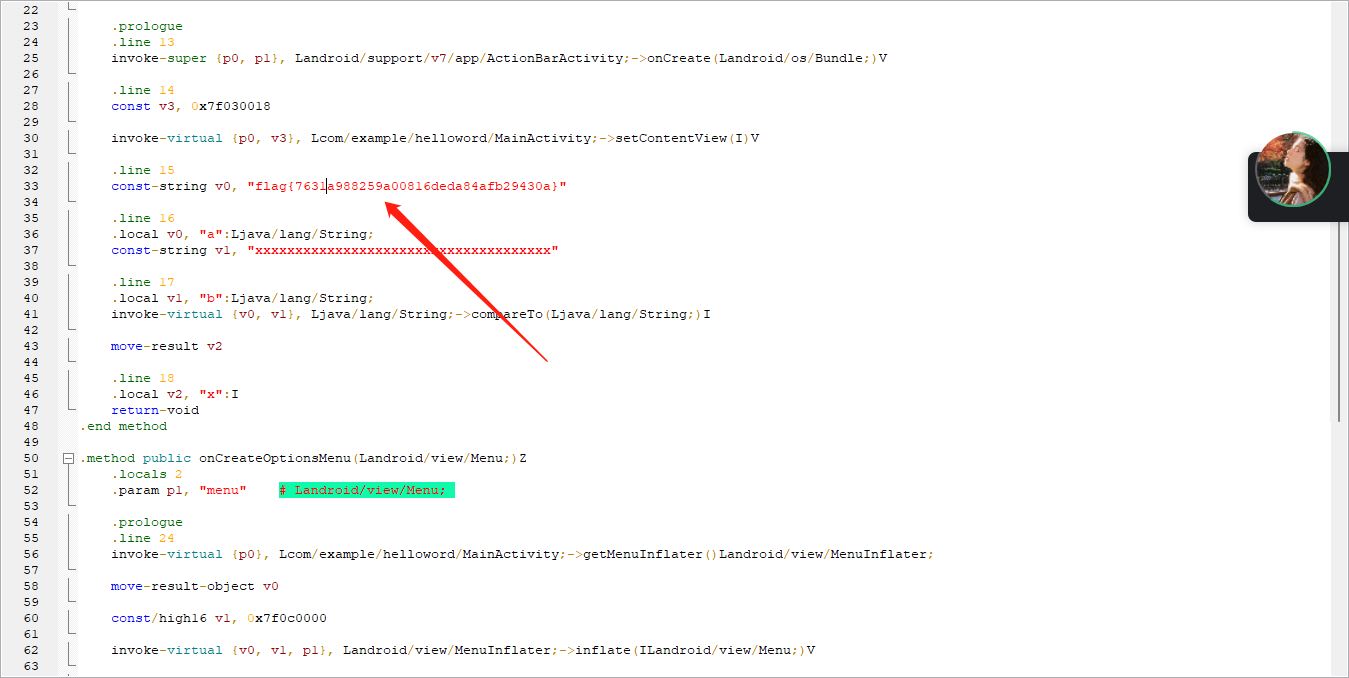
依次打开smali>com>example>helloword>MainActivity.smali
flag出来
reverse3
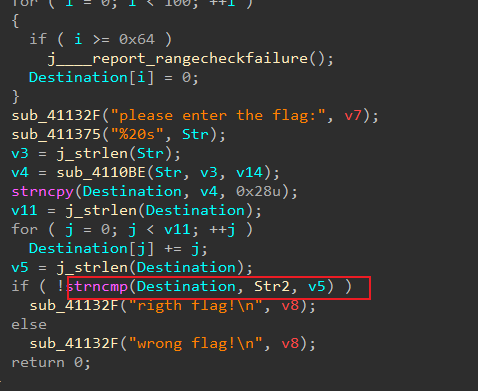
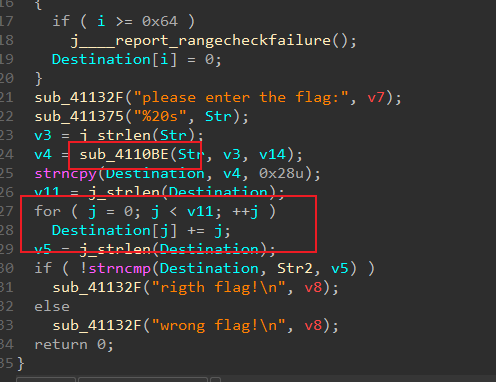
双击进入_main_0
f5查看伪代码
让后进去str2找到密文e3nifIH9b_C@n@dH
先base64 在异或+- 逆向倒着来写出脚本
1 2 3 4 5 6 7 8 import base64'e3nifIH9b_C@n@dH' '' for i in range (len (cipher)):chr ( ord (cipher[i] ) - i)print (base64.b64decode(result)
flag{i_l0ve_you}
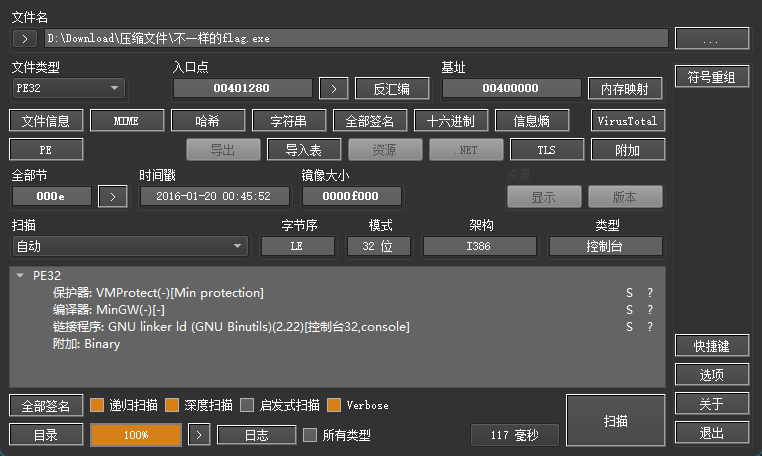
不一样的flag
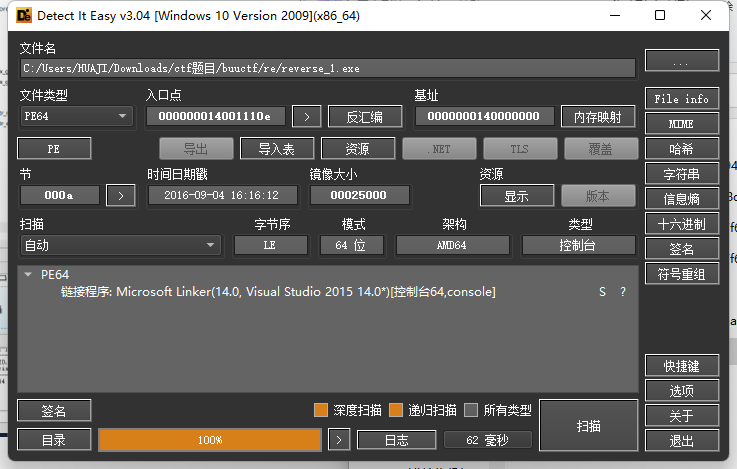
查看无壳
ida32 打开直接就是main
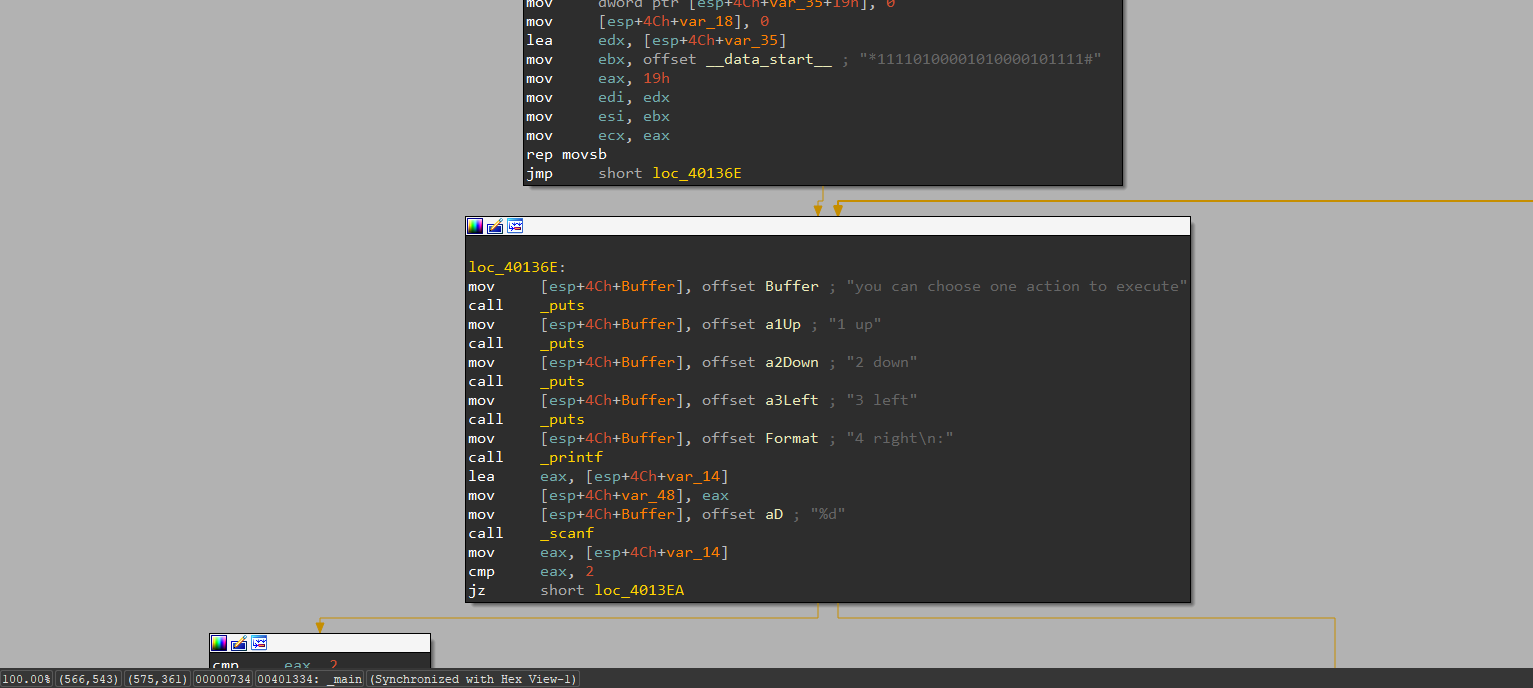
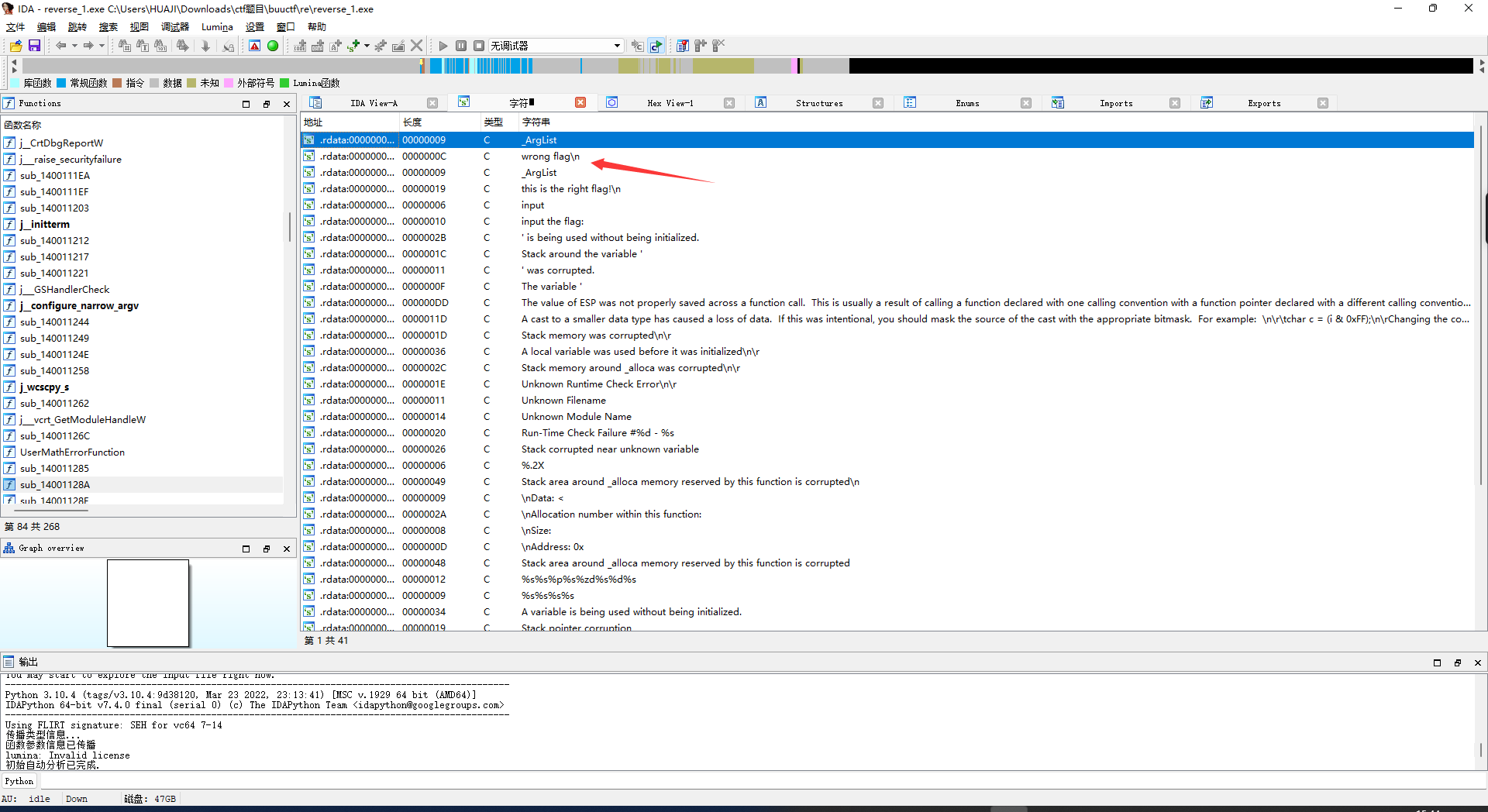
看到上写左右和一堆有规则的字符串猜测迷宫题目
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 *11110100001010000101111 # 源字符串 *1111 01000 01010 00010 1111 # 1 up 上2 down 下3 left 坐4 right 右
flag{222441144222}
SimpleRev
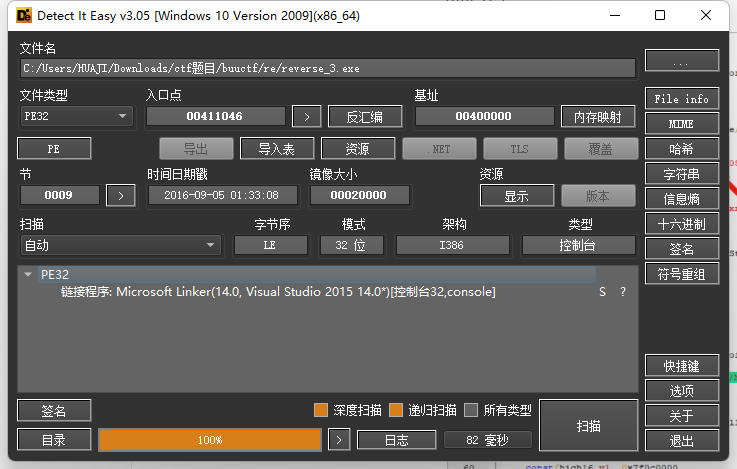
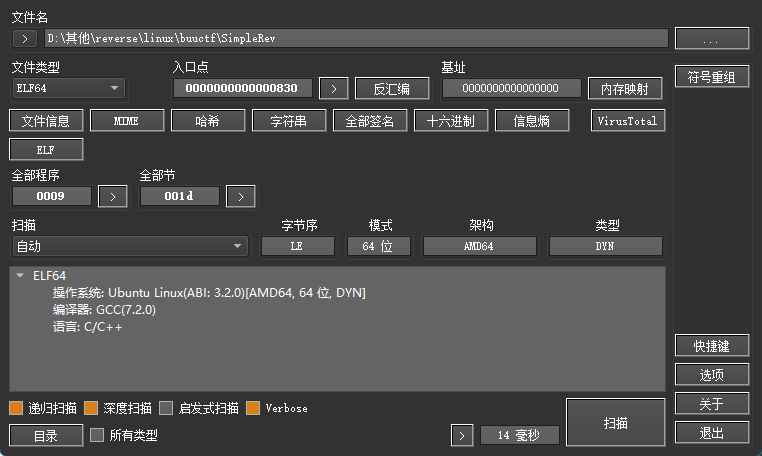
查克不存在发现是Linux 64位程序
让后使用ida64 打开调试发现 不行
一直都不能运行
让后
使用ida静态分析
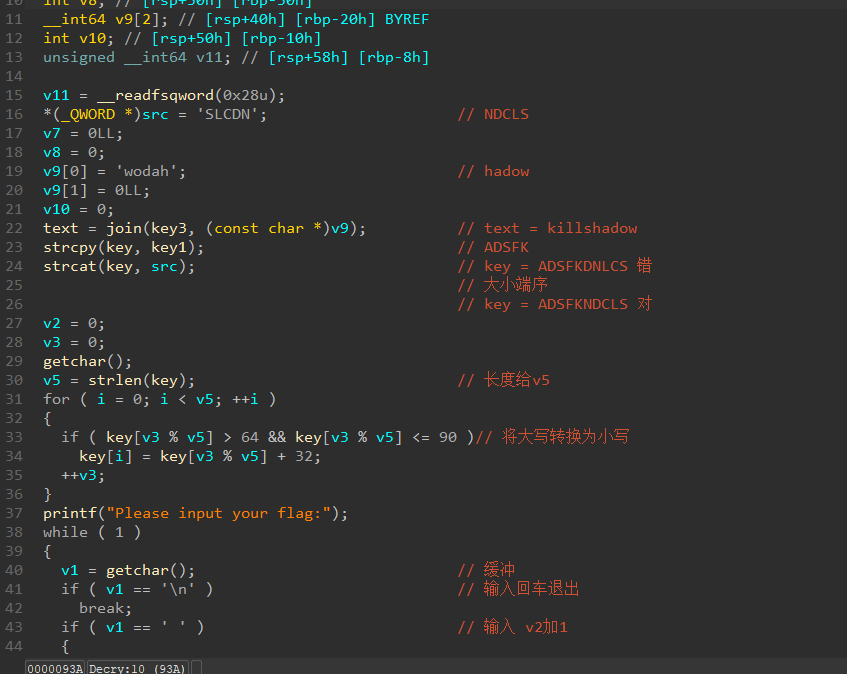
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 v11 = __readfsqword(0x28u);LCDN'; // NDCLSLL; LL; if ( key[v3 % v5] > 64 && key[v3 % v5] <= 90 )// 将大写转换为小写"Please input your flag:" ); if ( v1 == '\n' ) // 输入回车退出 if ( v1 == ' ' ) // 输入 v2加1 if ( v1 <= 96 || v1 > 122 ) // v1 小写 if ( v1 > 64 && v1 <= 90 ) // v1大写 if ( !(v3 % v5) ) if ( !strcmp(text, str2) )"Congratulation!\n" );"Try again!\n" ); return __readfsqword(0x28u) ^ v11;
让写出脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 import string "killshadow" key = "ADSFKNDCLS" key = str.lower(key ) # 转换小写string .ascii_uppercase + string .ascii_letters # 字典for i in range (len(cipher)):for j in dic:if (ord(j) - 39 - ord(key [i]) + 97 ) % 26 + 97 == ord(cipher[i]):append (j)break print ("flag{" + "" .join (result) + "}" )
flag{KLDQCUDFZO}
Java逆向解密 是一个.class文件使用jadx-gui 打开
看到encode
让后进入
写出逆向脚本
1 2 3 4 5 6 7 cipher = [180 , 136 , 137 , 147 , 191 , 137 , 147 , 191 , 148 , 136 , 133 , 191 , 134 , 140 , 129 , 135 , 191 , 65 ]0 ] * len (cipher)for i in range (len (cipher)):chr (cipher[i] - ord ('@' ) ^ 32 )print ("" .join(key))
#flag{This_is_the_flag_!}
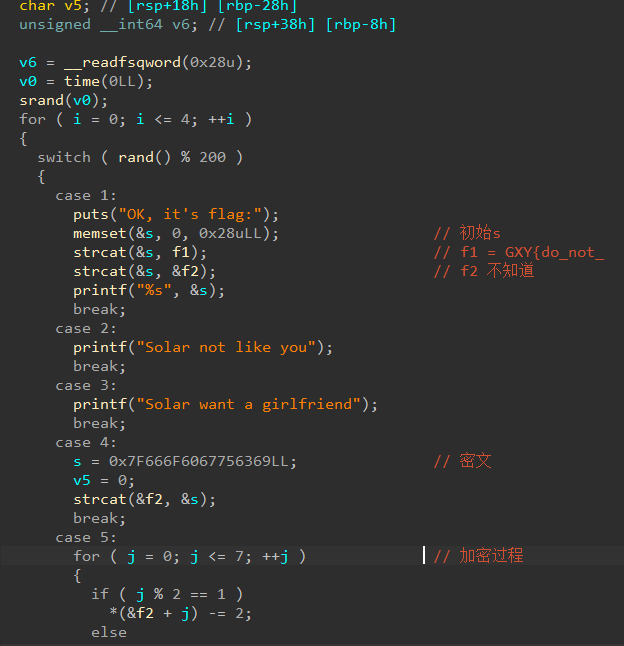
[GXYCTF2019]luck_guy 使用die 工具查壳 发现是64位 无壳子使用ida64 pro 打开
默认进入main 函数 让后发现没有什么操作直接去patch_me –> get-flag
密文[105, 99, 117, 103, 96, 111, 102, 127]
让后写出脚本
1 2 3 4 5 6 7 8 9 cipher = [105 , 99 , 117 , 103 , 96 , 111 , 102 , 127 ] result = '' for i in range(len (cipher)):if i % 2 == 1 :result += chr(cipher[i] -2 )else :result += chr(cipher[i] -1 )result )
GXY{do_not_hate_me}
 复制一份到剪贴板
复制一份到剪贴板